CS0-002 Exam Question 131
A company's computer was recently infected with ransomware. After encrypting all documents, the malware logs a random AES-128 encryption key and associated unique identifier onto a compromised remote website. A ransomware code snippet is shown below:
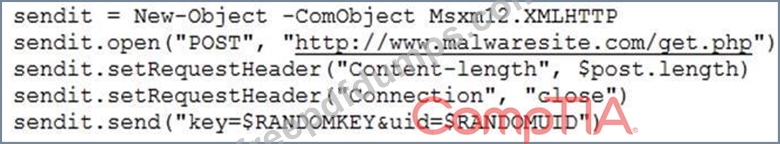
Based on the information from the code snippet, which of the following is the BEST way for a cybersecurity professional to monitor for the same malware in the future?

Based on the information from the code snippet, which of the following is the BEST way for a cybersecurity professional to monitor for the same malware in the future?
CS0-002 Exam Question 132
The help desk provided a security analyst with a screenshot of a user's desktop:
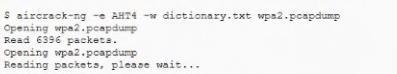
For which of the following is aircrack-ng being used?

For which of the following is aircrack-ng being used?
CS0-002 Exam Question 133
The security team at a large corporation is helping the payment-processing team to prepare for a regulatory compliance audit and meet the following objectives:
* Reduce the number of potential findings by the auditors.
* Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted by the regulations.
* Prevent the external-facing web infrastructure used by other teams from coming into scope.
* Limit the amount of exposure the company will face if the systems used by the payment-processing team are compromised.
Which of the following would be the MOST effective way for the security team to meet these objectives?
* Reduce the number of potential findings by the auditors.
* Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted by the regulations.
* Prevent the external-facing web infrastructure used by other teams from coming into scope.
* Limit the amount of exposure the company will face if the systems used by the payment-processing team are compromised.
Which of the following would be the MOST effective way for the security team to meet these objectives?
CS0-002 Exam Question 134
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues The steering committee wants to rank the risks based on past incidents to improve the security program for next year Below is the incident register for the organization.
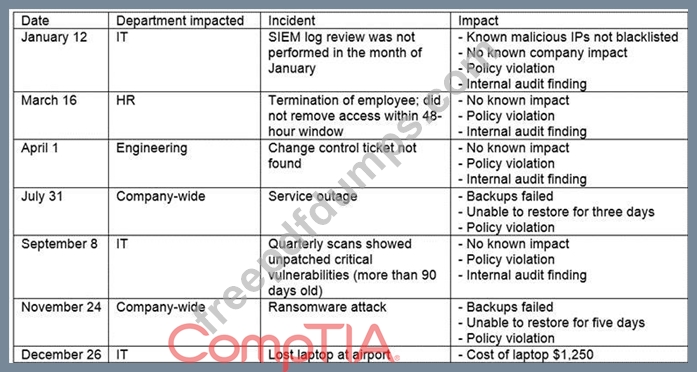
Which of the following should the organization consider investing in FIRST due to the potential impact of availability?

Which of the following should the organization consider investing in FIRST due to the potential impact of availability?
CS0-002 Exam Question 135
Which of the following types of controls defines placing an ACL on a file folder?

