CS0-002 Exam Question 146
A cybersecurity analyst is reviewing the following outputs:
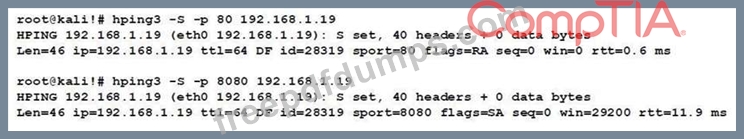
Which of the following can the analyst infer from the above output?

Which of the following can the analyst infer from the above output?
CS0-002 Exam Question 147
A Linux-based file encryption malware was recently discovered in the wild. Prior to running the malware on a preconfigured sandbox to analyze its behavior, a security professional executes the following command:
umount *a *t cifs,nfs
Which of the following is the main reason for executing the above command?
umount *a *t cifs,nfs
Which of the following is the main reason for executing the above command?
CS0-002 Exam Question 148
The inability to do remote updates of certificates, keys, software, and firmware is a security issue commonly associated with:
CS0-002 Exam Question 149
Ransomware is identified on a company's network that affects both Windows and MAC hosts. The command and control channel for encryption for this variant uses TCP ports from 11000 to 65000. The channel goes to good1. Iholdbadkeys.com, which resolves to IP address 72.172.16.2.
Which of the following is the MOST effective way to prevent any newly infected systems from actually encrypting the data on connected network drives while causing the least disruption to normal Internet traffic?
Which of the following is the MOST effective way to prevent any newly infected systems from actually encrypting the data on connected network drives while causing the least disruption to normal Internet traffic?
CS0-002 Exam Question 150
Given the following output from a Linux machine:
file2cable *i eth0 -f file.pcap
Which of the following BEST describes what a security analyst is trying to accomplish?
file2cable *i eth0 -f file.pcap
Which of the following BEST describes what a security analyst is trying to accomplish?

