CS0-002 Exam Question 156
When attempting to do a stealth scan against a system that does not respond to ping, which of the following Nmap commands BEST accomplishes that goal?
CS0-002 Exam Question 157
For machine learning to be applied effectively toward security analysis automation, it requires.
CS0-002 Exam Question 158
A small electronics company decides to use a contractor to assist with the development of a new FPGA-based device. Several of the development phases will occur off-site at the contractor's labs.
Which of the following is the main concern a security analyst should have with this arrangement?
Which of the following is the main concern a security analyst should have with this arrangement?
CS0-002 Exam Question 159
An employee was found to have performed fraudulent activities. The employee was dismissed, and the employee's laptop was sent to the IT service desk to undergo a data sanitization procedure. However, the security analyst responsible for the investigation wants to avoid data sanitization. Which of the following can the security analyst use to justify the request?
CS0-002 Exam Question 160
In order to the leverage the power of data correlation with Nessus, a cybersecurity analyst must first be able to create a table for the scan results.
Given the following snippet of code:
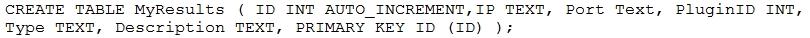
Which of the following output items would be correct?
Given the following snippet of code:
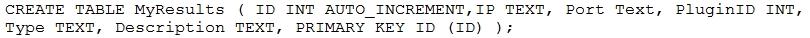
Which of the following output items would be correct?

