CS0-002 Exam Question 151
A Chief Executive Officer (CEO) is concerned about the company's intellectual property being leaked to competitors. The security team performed an extensive review but did not find any indication of an outside breach. The data sets are currently encrypted using the Triple Data Encryption Algorithm. Which of the following courses of action is appropriate?
CS0-002 Exam Question 152
After a breach involving the exfiltration of a large amount of sensitive data, a security analyst is reviewing the following firewall logs to determine how the breach occurred:
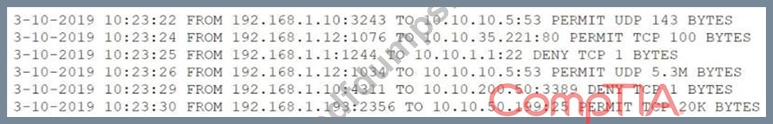
Which of the following IP addresses does the analyst need to investigate further?

Which of the following IP addresses does the analyst need to investigate further?
CS0-002 Exam Question 153
An analyst received a forensically sound copy of an employee's hard drive. The employee's manager suspects inappropriate images may have been deleted from the hard drive. Which of the following could help the analyst recover the deleted evidence?
CS0-002 Exam Question 154
Which of the following is the BEST way to gather patch information on a specific server?
CS0-002 Exam Question 155
industry partners from critical infrastructure organizations were victims of attacks on their SCADA devices. The attacks used privilege escalation to gain access to SCADA administration and access management solutions would help to mitigate this risk?

