CS0-002 Exam Question 166
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user.

Which of the following commands should the analyst investigate FIRST?

Which of the following commands should the analyst investigate FIRST?
CS0-002 Exam Question 167
An executive assistant wants to onboard a new cloud based product to help with business analytics and dashboarding. When of the following would be the BEST integration option for the service?
CS0-002 Exam Question 168
A company's modem response team is handling a threat that was identified on the network Security analysts have as at remote sites. Which of the following is the MOST appropriate next step in the incident response plan?
CS0-002 Exam Question 169
The Cruel Executive Officer (CEO) of a large insurance company has reported phishing emails that contain malicious links are targeting the entire organza lion Which of the following actions would work BEST to prevent against this type of attack?
CS0-002 Exam Question 170
While analyzing logs from a WAF, a cybersecurity analyst finds the following:
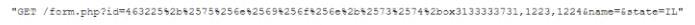
Which of the following BEST describes what the analyst has found?
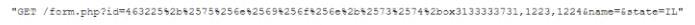
Which of the following BEST describes what the analyst has found?

