CS0-002 Exam Question 216
Creating a lessons learned report following an incident will help an analyst to communicate which of the following information? (Select TWO)
CS0-002 Exam Question 217
An employee was conducting research on the Internet when a message from cyber criminals appeared on the screen, stating the hard drive was just encrypted by a ransomware variant. An analyst observes the following:
Antivirus signatures were updated recently

The desktop background was changed

Web proxy logs show browsing to various information security sites and ad network traffic

There is a high volume of hard disk activity on the file server

SMTP server shown the employee recently received several emails from blocked senders

The company recently switched web hosting providers

There are several IPS alerts for external port scans

Which of the following describes how the employee got this type of ransomware?
Antivirus signatures were updated recently

The desktop background was changed

Web proxy logs show browsing to various information security sites and ad network traffic

There is a high volume of hard disk activity on the file server

SMTP server shown the employee recently received several emails from blocked senders

The company recently switched web hosting providers

There are several IPS alerts for external port scans

Which of the following describes how the employee got this type of ransomware?
CS0-002 Exam Question 218
industry partners from critical infrastructure organizations were victims of attacks on their SCADA devices. The attacks used privilege escalation to gain access to SCADA administration and access management solutions would help to mitigate this risk?
CS0-002 Exam Question 219
It is important to parameterize queries to prevent __________.
CS0-002 Exam Question 220
The help desk noticed a security analyst that emails from a new email server are not being sent out. The new email server was recently to the existing ones. The analyst runs the following command on the new server.
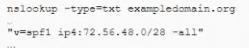
Given the output, which of the following should the security analyst check NEXT?

Given the output, which of the following should the security analyst check NEXT?

