CS0-002 Exam Question 201
As part of an upcoming engagement for a client, an analyst is configuring a penetration testing application to ensure the scan complies with information defined in the SOW.
Which of the following types of information should be considered based on information traditionally found in the SOW? (Select two.)
Which of the following types of information should be considered based on information traditionally found in the SOW? (Select two.)
CS0-002 Exam Question 202
A security analyst scanned an internal company subnet and discovered a host with the following Nmap output.
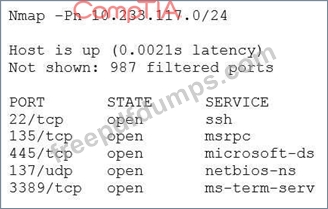
Based on the output of this Nmap scan, which of the following should the analyst investigate FIRST?

Based on the output of this Nmap scan, which of the following should the analyst investigate FIRST?
CS0-002 Exam Question 203
A new on-premises application server was recently installed on the network. Remote access to the server was enabled for vendor support on required ports, but recent security reports show large amounts of data are being sent to various unauthorized networks through those ports. Which of the following configuration changes must be implemented to resolve this security issue while still allowing remote vendor access?
CS0-002 Exam Question 204
Which of the following BEST describes the primary role ol a risk assessment as it relates to compliance with risk-based frameworks?
CS0-002 Exam Question 205
The Dirty COW attack is an example of what type of vulnerability?

