CS0-002 Exam Question 331
A cybersecurity analyst is currently checking a newly deployed server that has an access control list applied.
When conducting the scan, the analyst received the following code snippet of results:
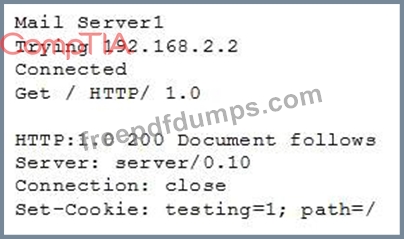
Which of the following describes the output of this scan?
When conducting the scan, the analyst received the following code snippet of results:

Which of the following describes the output of this scan?
CS0-002 Exam Question 332
Which of the following utilities could be used to resolve an IP address to a domain name, assuming the address has a PTR record?
CS0-002 Exam Question 333
A company wants to establish a threat-hunting team. Which of the following BEST describes the rationale for integrating intelligence into hunt operations?
CS0-002 Exam Question 334
While preparing of an audit of information security controls in the environment an analyst outlines a framework control that has the following requirements:
* All sensitive data must be classified
* All sensitive data must be purged on a quarterly basis
* Certificates of disposal must remain on file for at least three years This framework control is MOST likely classified as:
* All sensitive data must be classified
* All sensitive data must be purged on a quarterly basis
* Certificates of disposal must remain on file for at least three years This framework control is MOST likely classified as:
CS0-002 Exam Question 335
An analyst identifies multiple instances of node-to-node communication between several endpoints within the 10.200.2.0/24 network and a user machine at the IP address 10.200.2.5. This user machine at the IP address 10.200.2.5 is also identified as initiating outbound communication during atypical business hours with several IP addresses that have recently appeared on threat feeds.
Which of the following can be inferred from this activity?
Which of the following can be inferred from this activity?

