CS0-002 Exam Question 336
An analyst is detecting Linux machines on a Windows network. Which of the following tools should be used to detect a computer operating system?
CS0-002 Exam Question 337
A security analyst is researching an incident and uncovers several details that may link to other incidents. The security analyst wants to determine if other incidents are related to the current incident Which of the followinq threat research methodoloqies would be MOST appropriate for the analyst to use?
CS0-002 Exam Question 338
After running a packet analyzer on the network, a security analyst has noticed the following output:
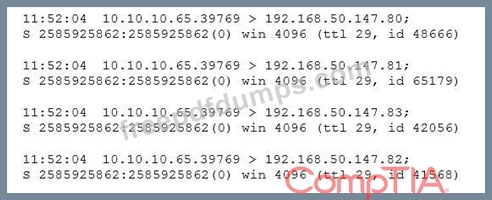
Which of the following is occurring?

Which of the following is occurring?
CS0-002 Exam Question 339
An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output:
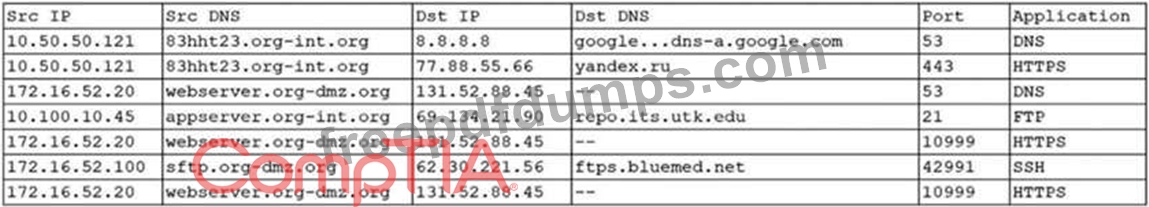
Which of the following should be the focus of the investigation?

Which of the following should be the focus of the investigation?
CS0-002 Exam Question 340
A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities. The type of vulnerability that should be disseminated FIRST is one that:

