CS0-002 Exam Question 116
Which of the following is the software development process by which function, usability, and scenarios are tested against a known set of base requirements?
CS0-002 Exam Question 117
A security analyst is reviewing packet captures for a specific server that is suspected of containing malware and discovers the following packets:
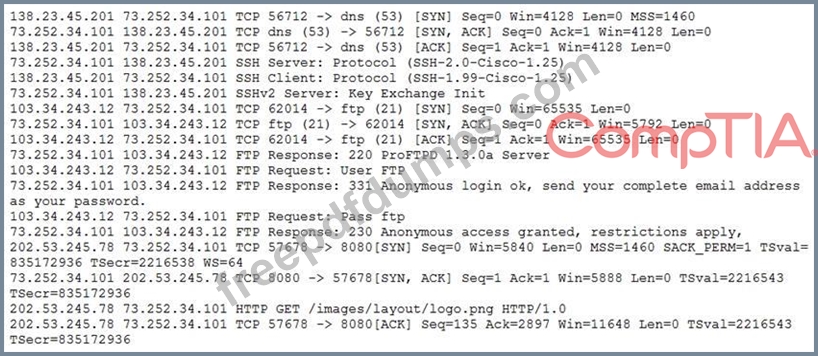
Which of the following traffic patterns or data would be MOST concerning to the security analyst?

Which of the following traffic patterns or data would be MOST concerning to the security analyst?
CS0-002 Exam Question 118
A cybersecurity analyst wants to use ICMP ECHO_REQUEST on a machine while using Nmap.
Which of the following is the correct command to accomplish this?
Which of the following is the correct command to accomplish this?
CS0-002 Exam Question 119
A development team is testing a new application release. The team needs to import existing client PHI data records from the production environment to the test environment to test accuracy and functionality.
Which of the following would BEST protect the sensitivity of this data while still allowing the team to perform the testing?
Which of the following would BEST protect the sensitivity of this data while still allowing the team to perform the testing?
CS0-002 Exam Question 120
A company has contracted with a software development vendor to design a web portal for customers to access a medical records database. Which of the following should the security analyst recommend to BEST control the unauthorized disclosure of sensitive data when sharing the development database with the vendor?

