CS0-002 Exam Question 176
A company invested ten percent of its entire annual budget in security technologies. The Chief Information Officer (CIO) is convinced that, without this investment, the company will risk being the next victim of the same cyber attack its competitor experienced three months ago. However, despite this investment, users are sharing their usernames and passwords with their coworkers to get their jobs done. Which of the following will eliminate the risk introduced by this practice?
CS0-002 Exam Question 177
It is important to parameterize queries to prevent:
CS0-002 Exam Question 178
A security analyst is investigating a compromised Linux server.
The analyst issues the ps command and receives the following output.
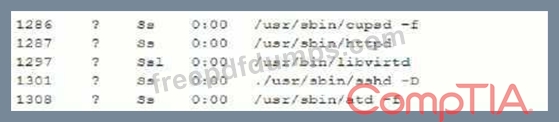
Which of the following commands should the administrator run NEXT to further analyze the compromised system?
The analyst issues the ps command and receives the following output.

Which of the following commands should the administrator run NEXT to further analyze the compromised system?
CS0-002 Exam Question 179
Which of the following is the MOST secure method to perform dynamic analysis of malware that can sense when it is in a virtual environment?
CS0-002 Exam Question 180
The Chief Security Officer (CSO) has requested a vulnerability report of systems on the domain, identifying those running outdated OSs. The automated scan reports are not displaying OS version details, so the CSO cannot determine risk exposure levels from vulnerable systems.
Which of the following should the cybersecurity analyst do to enumerate OS information as part of the vulnerability scanning process in the MOST efficient manner?
Which of the following should the cybersecurity analyst do to enumerate OS information as part of the vulnerability scanning process in the MOST efficient manner?

