CS0-002 Exam Question 186
A security analyst is preparing for the company's upcoming audit. Upon review of the company's latest vulnerability scan, the security analyst finds the following open issues:
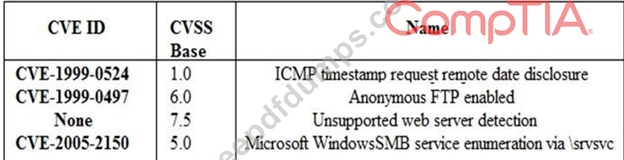
Which of the following vulnerabilities should be prioritized for remediation FIRST?

Which of the following vulnerabilities should be prioritized for remediation FIRST?
CS0-002 Exam Question 187
A security analyst recently discovered two unauthorized hosts on the campus's wireless network segment from a man-in-the-middle attack. The security analyst also verified that privileges were not escalated, and the two devices did not gain access to other network devices. Which of the following would BEST mitigate and improve the security posture of the wireless network for this type of attack?
CS0-002 Exam Question 188
A company's Chief Information Security Officer (CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user's activity session. Which of the following is the BEST technique to address the CISO's concerns?
CS0-002 Exam Question 189
A security analyst received an alert from the SIEM indicating numerous login attempts from users outside their usual geographic zones, all of which were initiated through the web-based mail server. The logs indicate all domain accounts experienced two login attempts during the same time frame.
Which of the following is the MOST likely cause of this issue?
Which of the following is the MOST likely cause of this issue?
CS0-002 Exam Question 190
A security analyst is investigating a compromised Linux server. The analyst issues the ps command and receives the following output.

Which of the following commands should the administrator run NEXT to further analyze the compromised system?

Which of the following commands should the administrator run NEXT to further analyze the compromised system?

