CS0-002 Exam Question 181
A cybersecurity analyst traced the source of an attack to compromised user credentials. Log analysis revealed that the attacker successfully authenticated from an unauthorized foreign country. Management asked the security analyst to research and implement a solution to help mitigate attacks based on compromised passwords.
Which of the following should the analyst implement?
Which of the following should the analyst implement?
CS0-002 Exam Question 182
An analyst is working with a network engineer to resolve a vulnerability that was found in a piece of legacy hardware, which is critical to the operation of the organization's production line. The legacy hardware does not have third-party support, and the OEM manufacturer of the controller is no longer in operation. The analyst documents the activities and verifies these actions prevent remote exploitation of the vulnerability.
Which of the following would be the MOST appropriate to remediate the controller?
Which of the following would be the MOST appropriate to remediate the controller?
CS0-002 Exam Question 183
After completing a vulnerability scan, the following output was noted:
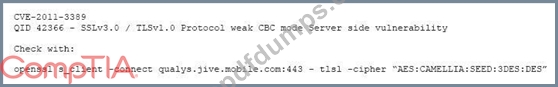
Which of the following vulnerabilities has been identified?

Which of the following vulnerabilities has been identified?
CS0-002 Exam Question 184
An analyst wants to use a command line tool to identify open ports and running services on a host along with the application that is associated with those services and port.
Which of the following should the analyst use?
Which of the following should the analyst use?
CS0-002 Exam Question 185
A security analyst is running a routine vulnerability scan against a web farm. The farm consists of a single server acting as a load-balancing reverse proxy and offloads cryptographic processes to the backend servers. The backend servers consist of four servers that process the inquiries for the front end.
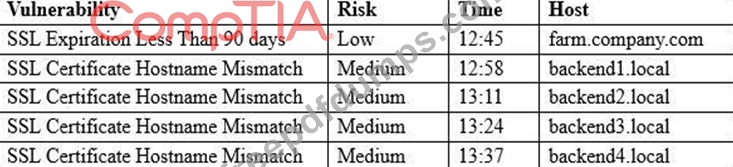
A web service SSL query of each server responds with the same output:
Connected (0x000003)
depth=0 /0=farm.company.com/CN=farm.company.com/OU=Domain Control Validated Which of the following results BEST addresses these findings?

A web service SSL query of each server responds with the same output:
Connected (0x000003)
depth=0 /0=farm.company.com/CN=farm.company.com/OU=Domain Control Validated Which of the following results BEST addresses these findings?

