CS0-002 Exam Question 346
While reviewing proxy logs, the security analyst noticed a suspicious traffic pattern. Several internal hosts were observed communicating with an external IP address over port 80 constantly.
An incident was declared, and an investigation was launched. After interviewing the affected users, the analyst determined the activity started right after deploying a new graphic design suite.
Based on this information, which of the following actions would be the appropriate NEXT step in the investigation?
An incident was declared, and an investigation was launched. After interviewing the affected users, the analyst determined the activity started right after deploying a new graphic design suite.
Based on this information, which of the following actions would be the appropriate NEXT step in the investigation?
CS0-002 Exam Question 347
A small organization has proprietary software that is used internally. The system has not been well maintained and cannot be updated with the rest of the environment Which of the following is the BEST solution?
CS0-002 Exam Question 348
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server.
Suspecting the system may be compromised, the analyst runs the following commands:
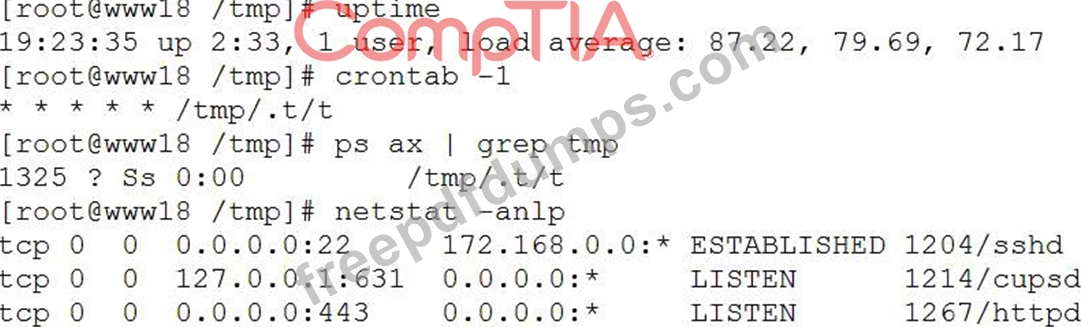
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
Suspecting the system may be compromised, the analyst runs the following commands:

Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
CS0-002 Exam Question 349
The security team at a large corporation is helping the payment-processing team to prepare for a regulatory compliance audit and meet the following objectives:
- Reduce the number of potential findings by the auditors.
- Limit the scope of the audit to only devices used by the payment-
processing team for activities directly impacted by the regulations.
- Prevent the external-facing web infrastructure used by other teams
from coming into scope.
- Limit the amount of exposure the company will face if the systems
used by the payment-processing team are compromised.
Which of the following would be the MOST effective way for the security team to meet these objectives?
- Reduce the number of potential findings by the auditors.
- Limit the scope of the audit to only devices used by the payment-
processing team for activities directly impacted by the regulations.
- Prevent the external-facing web infrastructure used by other teams
from coming into scope.
- Limit the amount of exposure the company will face if the systems
used by the payment-processing team are compromised.
Which of the following would be the MOST effective way for the security team to meet these objectives?
CS0-002 Exam Question 350
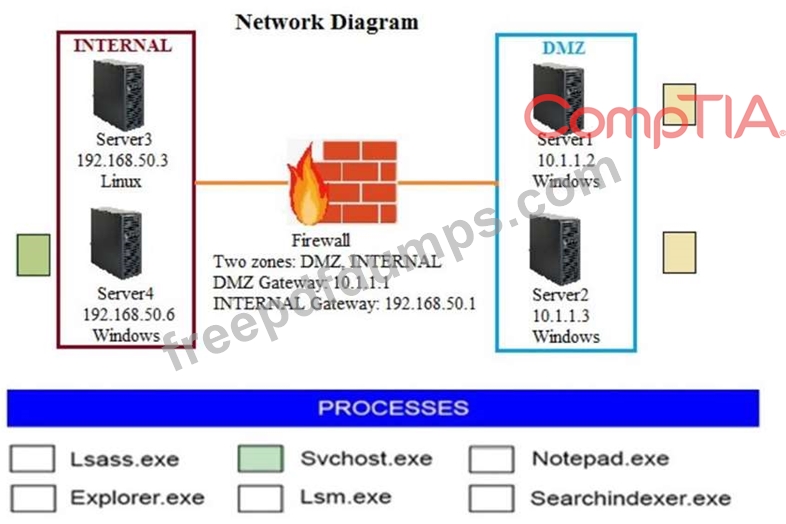
Hotspot Question
Malware is suspected on a server in the environment. The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware. Servers 1, 2 and 4 are clickable. Select the Server which hosts the malware, and select the process which hosts this malware.
Instructions:
If any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
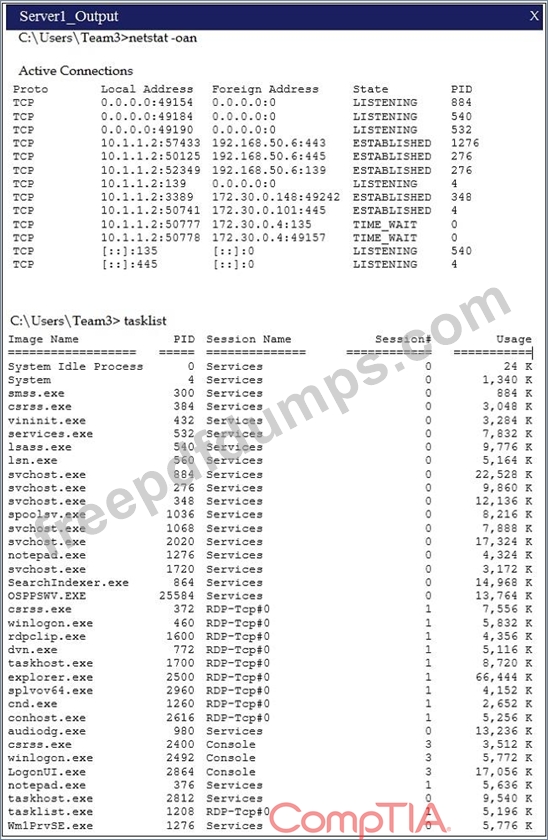
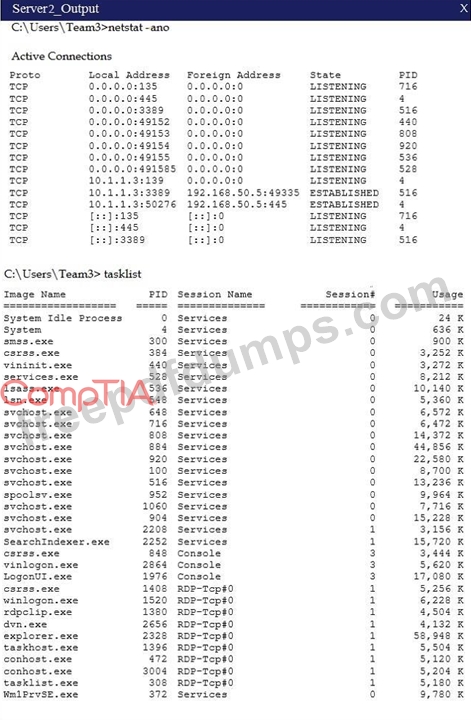
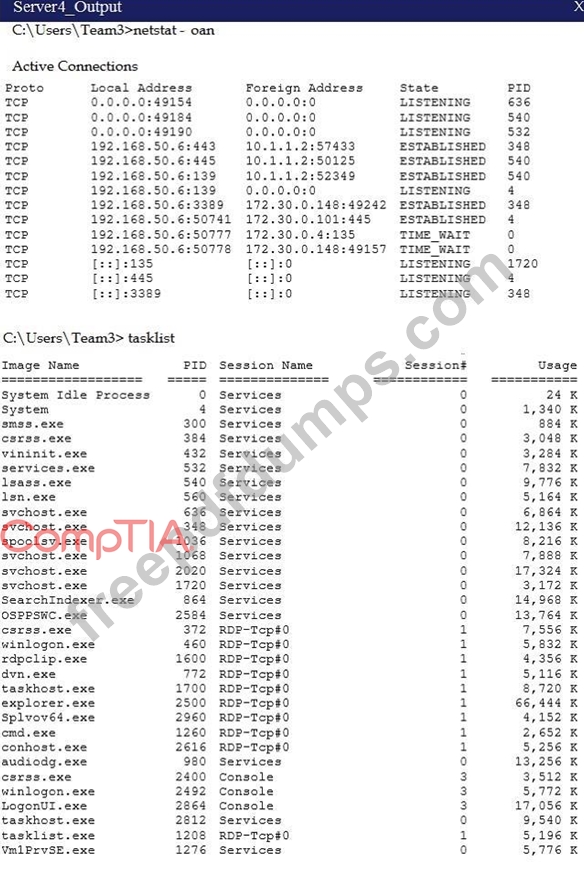
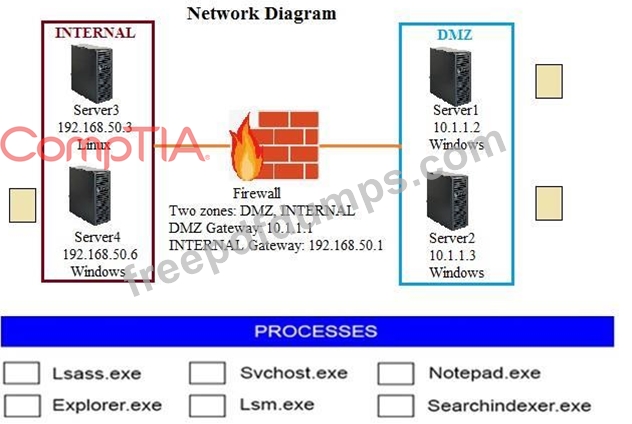
Malware is suspected on a server in the environment. The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware. Servers 1, 2 and 4 are clickable. Select the Server which hosts the malware, and select the process which hosts this malware.
Instructions:
If any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.