CS0-002 Exam Question 351
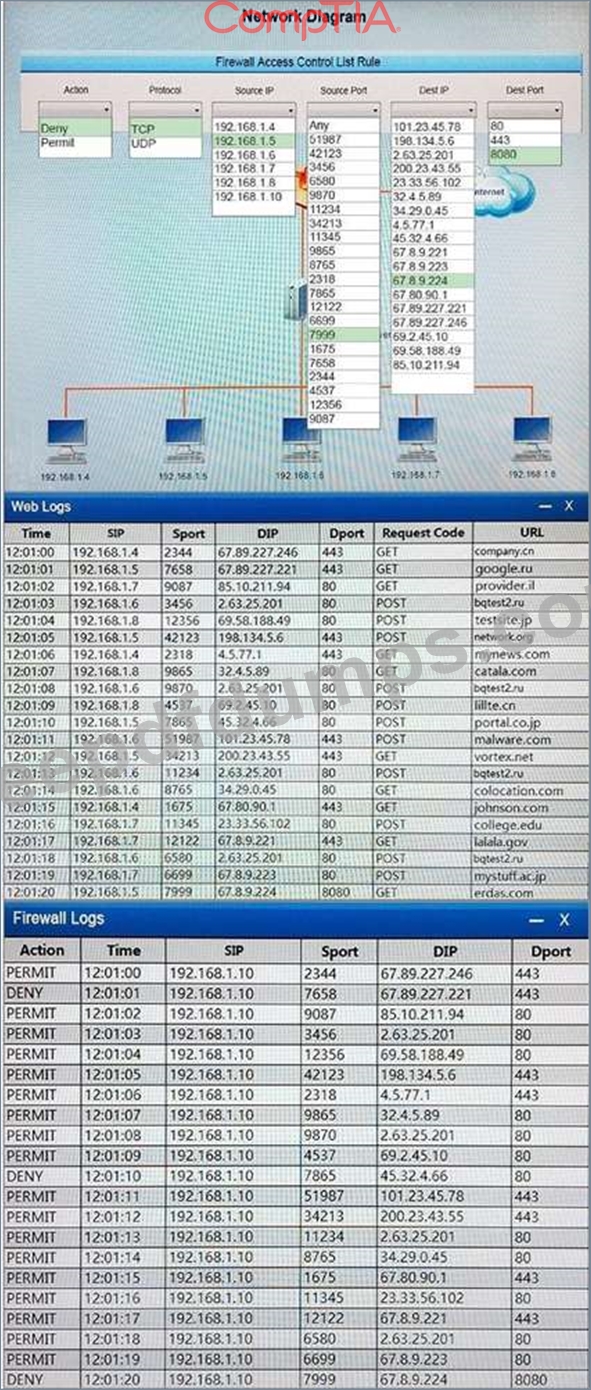
The help desk provided a security analyst with a screenshot of a user's desktop:
For which of the following is aircrack-ng being used?

For which of the following is aircrack-ng being used?
CS0-002 Exam Question 352
Hotspot Question
A security analyst suspects that a workstation may be beaconing to a command and control server.
You must inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
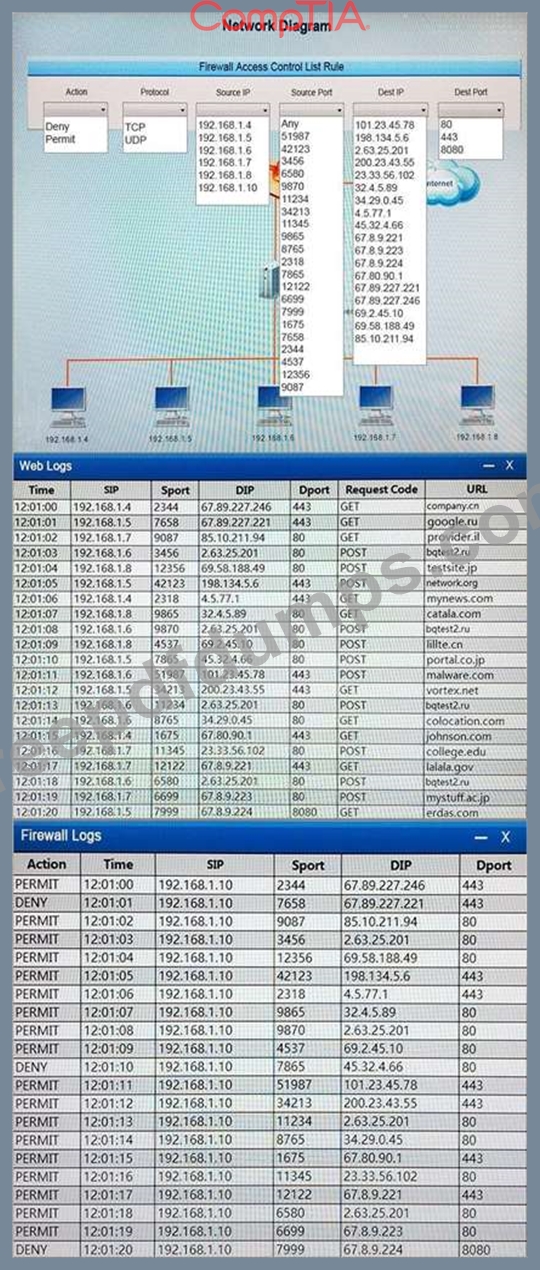
A security analyst suspects that a workstation may be beaconing to a command and control server.
You must inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

CS0-002 Exam Question 353
The help desk noticed a security analyst that emails from a new email server are not being sent out. The new email server was recently to the existing ones. The analyst runs the following command on the new server.
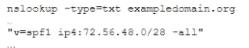
Given the output, which of the following should the security analyst check NEXT?

Given the output, which of the following should the security analyst check NEXT?
CS0-002 Exam Question 354
A security analyst is building a malware analysis lab. The analyst wants to ensure malicious applications are not capable of escaping the virtual machines and pivoting to other networks.
To BEST mitigate this risk, the analyst should use .
To BEST mitigate this risk, the analyst should use .
CS0-002 Exam Question 355
Weeks before a proposed merger is scheduled for completion, a security analyst has noticed unusual traffic patterns on a file server that contains financial information. Routine scans are not detecting the signature of any known exploits or malware. The following entry is seen in the ftp server logs:
tftp *I 10.1.1.1 GET fourthquarterreport.xls
Which of the following is the BEST course of action?
tftp *I 10.1.1.1 GET fourthquarterreport.xls
Which of the following is the BEST course of action?