CS0-002 Exam Question 361
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server. Suspecting the system may be compromised, the analyst runs the following commands:
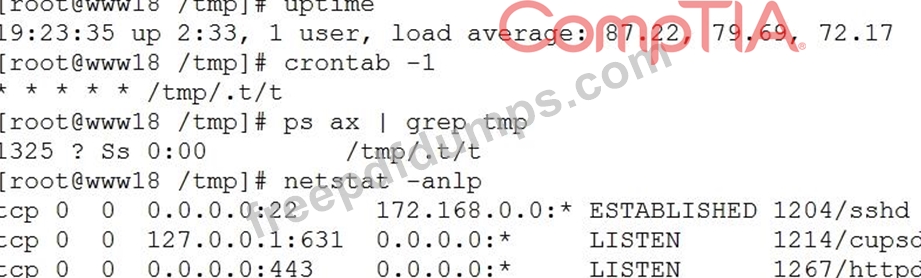
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?

Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
CS0-002 Exam Question 362
Which of the following is the BEST security practice to prevent ActiveX controls from running malicious code on a user's web application?
CS0-002 Exam Question 363
An analyst receives artifacts from a recent Intrusion and is able to pull a domain, IP address, email address, and software version. When of the following points of the Diamond Model of Intrusion Analysis does this intelligence represent?
CS0-002 Exam Question 364
A security analyst is investigating a compromised Linux server. The analyst issues the ps command and receives the following output.
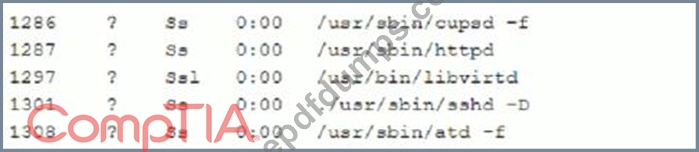
Which of the following commands should the administrator run NEXT to further analyze the compromised system?

Which of the following commands should the administrator run NEXT to further analyze the compromised system?
CS0-002 Exam Question 365
Which of the following commands would a security analyst use to make a copy of an image for forensics use?

