CS0-002 Exam Question 381
An analyst is investigating an anomalous event reported by the SOC After reviewing the system logs the analyst identifies an unexpected addition of a user with root-level privileges on the endpoint. Which of the following data sources will BEST help the analyst to determine whether this event constitutes an incident?
CS0-002 Exam Question 382
The Chief Information Security Officer (CISO) asked for a topology discovery to be conducted and verified against the asset inventory. The discovery is failing and not providing reliable or complete data. The syslog shows the following information:
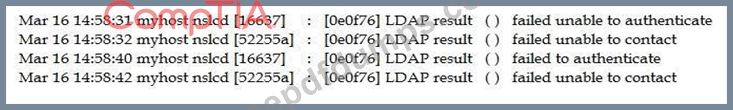
Which of the following describes the reason why the discovery is failing?

Which of the following describes the reason why the discovery is failing?
CS0-002 Exam Question 383
An organization has a policy prohibiting remote administration of servers where web services are running.
One of the Nmap scans is shown here:
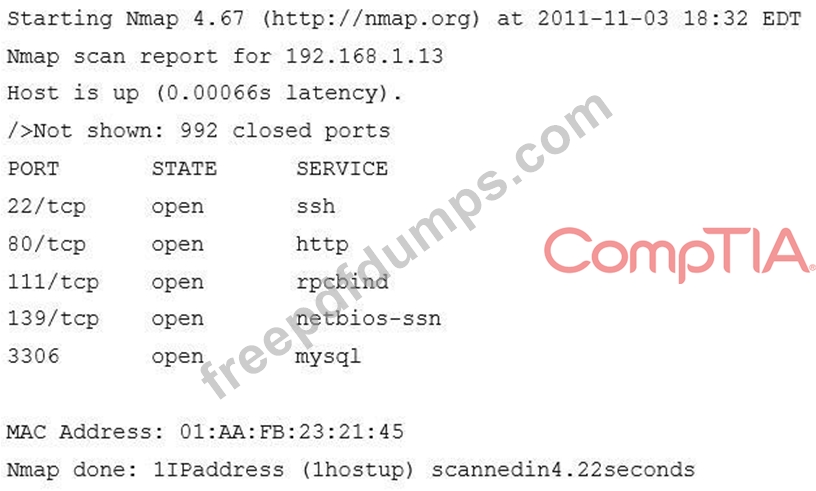
Given the organization's policy, which of the following services should be disabled on this server?
One of the Nmap scans is shown here:

Given the organization's policy, which of the following services should be disabled on this server?
CS0-002 Exam Question 384
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server.
Tool A reported the following:
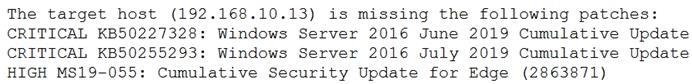
Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Tool A reported the following:

Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
CS0-002 Exam Question 385
As part of an Intelligence feed, a security analyst receives a report from a third-party trusted source. Within the report are several detrains and reputational information that suggest the company's employees may be targeted for a phishing campaign. Which of the following configuration changes would be the MOST appropriate for Mergence gathering?

