CS0-002 Exam Question 386
A security analyst is reviewing the logs from an internal chat server. The chat.log file is too large to review manually, so the analyst wants to create a shorter log file that only includes lines associated with a user demonstrating anomalous activity. Below is a snippet of the log:
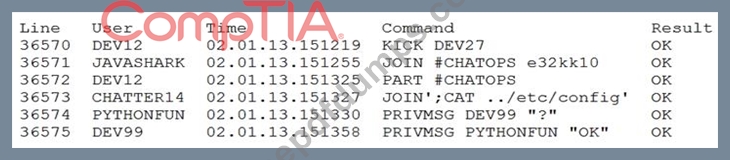
Which of the following commands would work BEST to achieve the desired result?

Which of the following commands would work BEST to achieve the desired result?
CS0-002 Exam Question 387
The help desk informed a security analyst of a trend that is beginning to develop regarding a suspicious email that has been reported by multiple users.
The analyst has determined the email includes an attachment named invoice.zip that contains the following files:
Locky.js

xerty.ini

xerty.lib

Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices.
Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices?
The analyst has determined the email includes an attachment named invoice.zip that contains the following files:
Locky.js

xerty.ini

xerty.lib

Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices.
Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices?
CS0-002 Exam Question 388
A company installed a wireless network more than a year ago, standardizing on the same model APs in a single subnet. Recently, several users have reported timeouts and connection issues with Internet browsing. The security administrator has gathered some information about the network to try to recreate the issues with the assistance of a user. The administrator is able to ping every device on the network and confirms that the network is very slow.

Output:
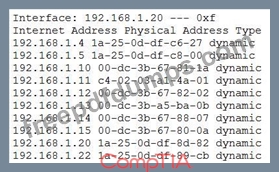
Given the above results, which of the following should the administrator investigate FIRST?

Output:

Given the above results, which of the following should the administrator investigate FIRST?
CS0-002 Exam Question 389
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server.
Suspecting the system may be compromised, the analyst runs the following commands:
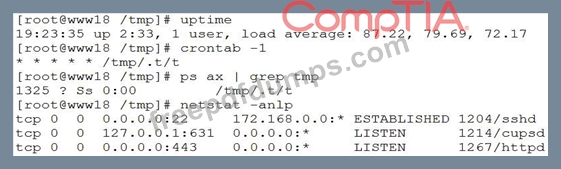
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
Suspecting the system may be compromised, the analyst runs the following commands:

Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
CS0-002 Exam Question 390
The software development team pushed a new web application into production for the accounting department. Shortly after the application was published, the head of the accounting department informed IT operations that the application was not performing as intended. Which of the following SDLC best practices was missed?

