CS0-002 Exam Question 121
An organization is requesting the development of a disaster recovery plan.
The organization has grown and so has its infrastructure.
Documentation, policies, and procedures do not exist.
Which of the following steps should be taken to assist in the development of the disaster recovery plan?
The organization has grown and so has its infrastructure.
Documentation, policies, and procedures do not exist.
Which of the following steps should be taken to assist in the development of the disaster recovery plan?
CS0-002 Exam Question 122
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server.
Suspecting the system may be compromised, the analyst runs the following commands:
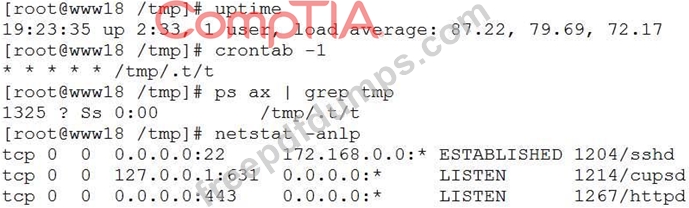
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
Suspecting the system may be compromised, the analyst runs the following commands:

Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
CS0-002 Exam Question 123
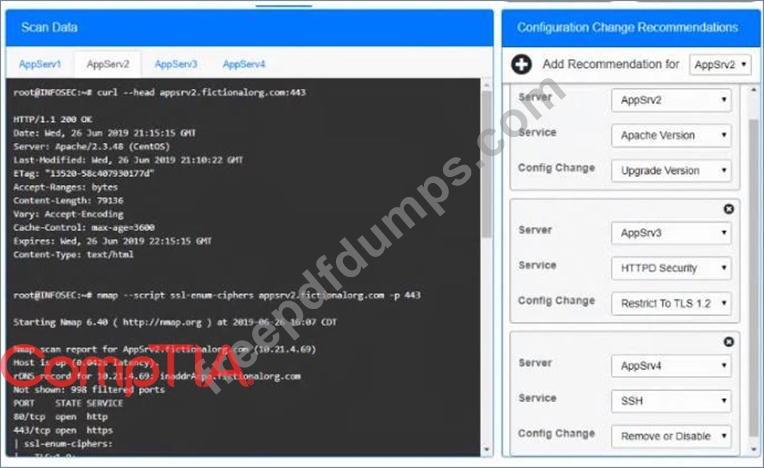
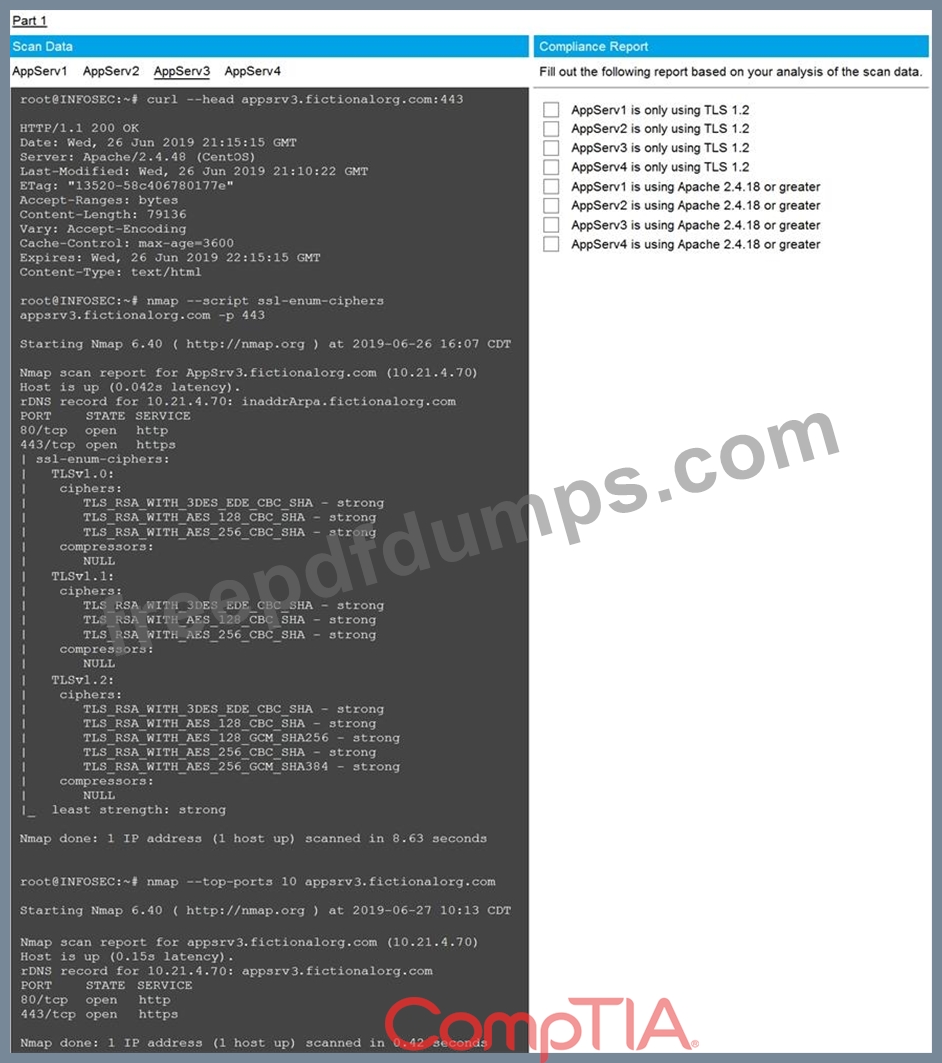
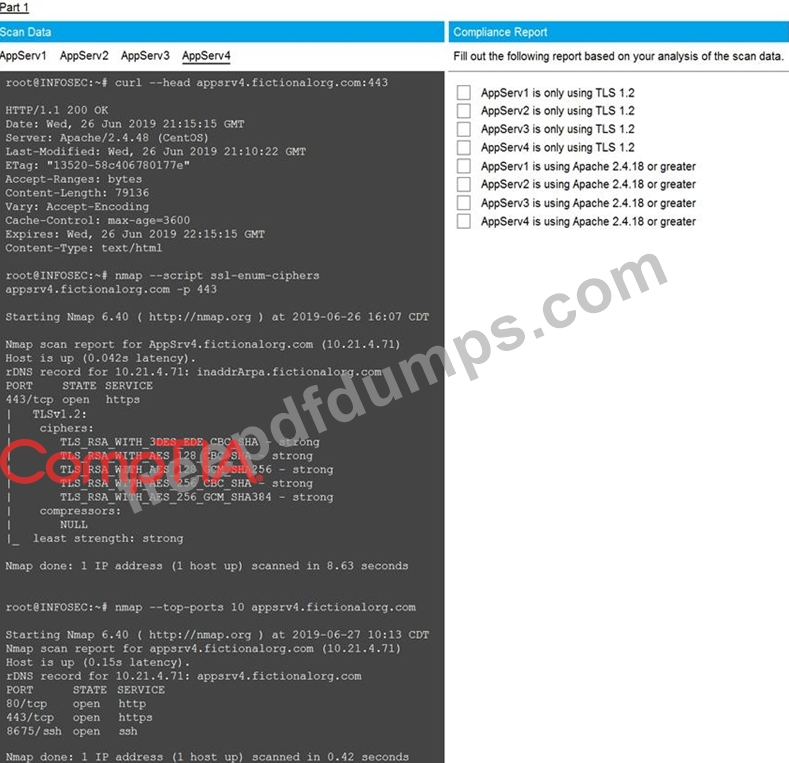
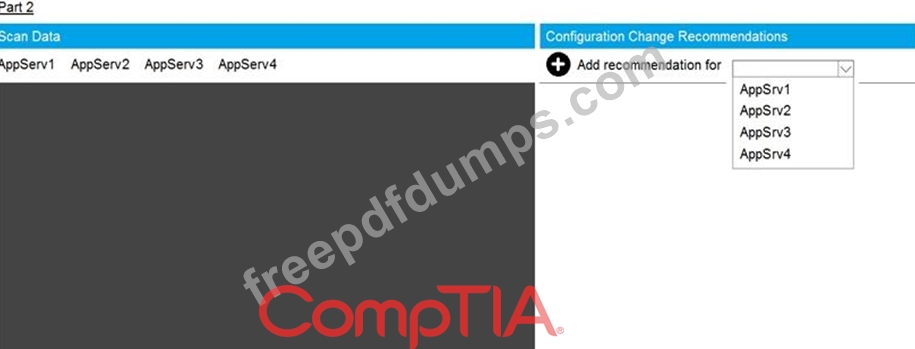
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not.
The company's hardening guidelines indicate the following:
* TLS 1.2 is the only version of TLS running.
* Apache 2.4.18 or greater should be used.
* Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
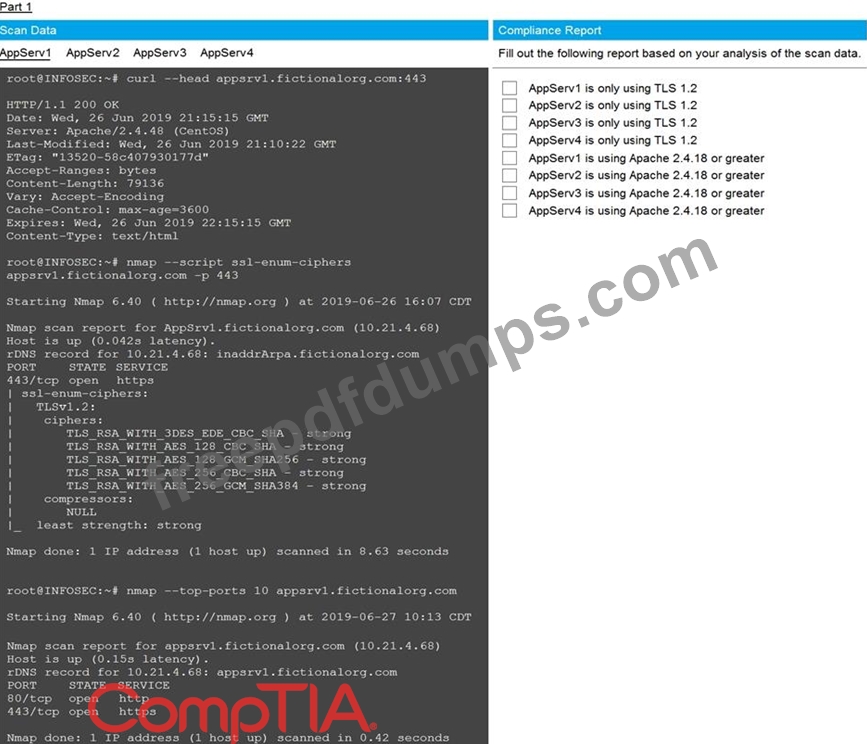
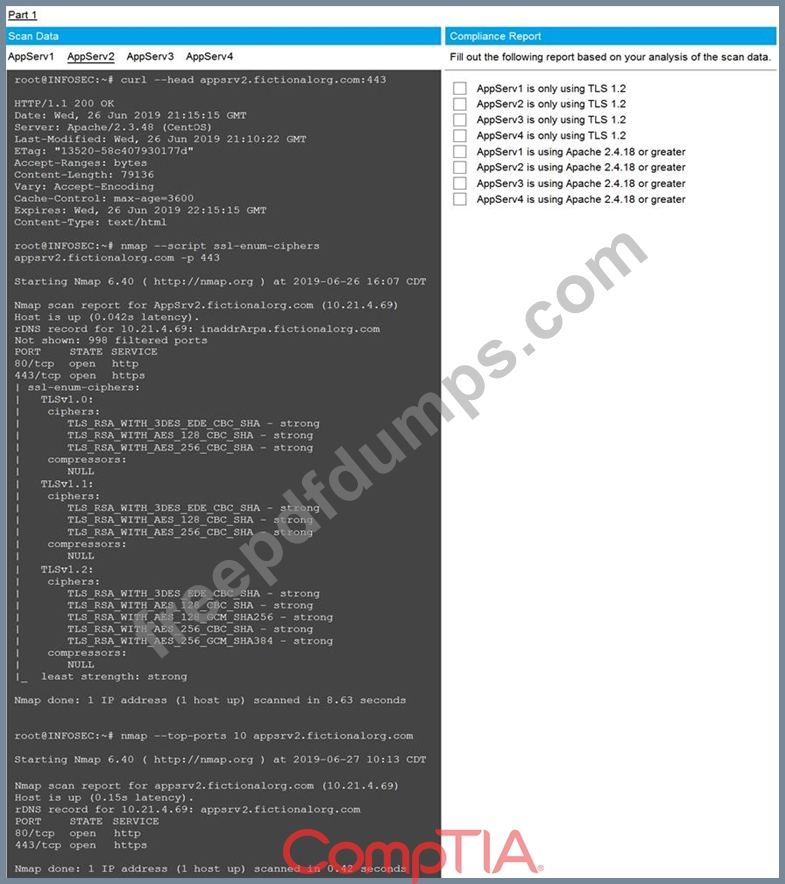
The company's hardening guidelines indicate the following:
* TLS 1.2 is the only version of TLS running.
* Apache 2.4.18 or greater should be used.
* Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.





CS0-002 Exam Question 124
A security analyst recently discovered two unauthorized hosts on the campus's wireless network segment from a man-m-the-middle attack.
The security analyst also verified that privileges were not escalated, and the two devices did not gain access to other network devices.
Which of the following would BEST mitigate and improve the security posture of the wireless network for this type of attack?
The security analyst also verified that privileges were not escalated, and the two devices did not gain access to other network devices.
Which of the following would BEST mitigate and improve the security posture of the wireless network for this type of attack?
CS0-002 Exam Question 125
An organization recently discovered some inconsistencies in the motherboards it received from a vendor. The organization's security team then provided guidance on how to ensure the authenticity of the motherboards it received from vendors.
Which of the following would be the BEST recommendation for the security analyst to provide'?
Which of the following would be the BEST recommendation for the security analyst to provide'?