CKS Exam Question 1
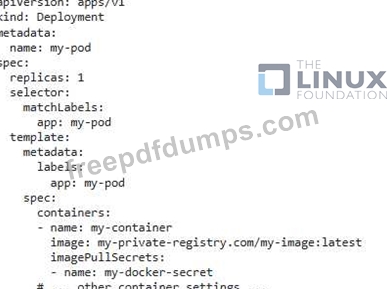
You need to create a Kubernetes secret that stores a password and use that secret to access a private Docker registry during pod deployment. Describe the steps you would take to create the secret and deploy a pod using the secret to pull an image from the private registry.
CKS Exam Question 2
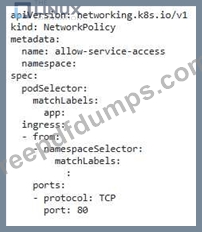
You have a Kubernetes cluster with a deployment running a critical application. You need to restrict inbound network access to the pods in this deployment to only allow traffic from a specific service within the cluster. How would you achieve this using NetworkPolicy?
CKS Exam Question 3
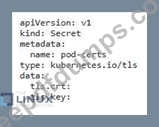
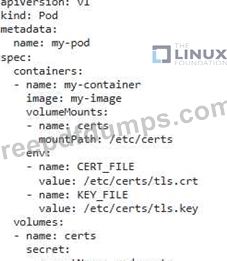
You are responsible for securing a Kubernetes cluster that hosts sensitive dat
a. You need to ensure that all communication between pods within the cluster is encrypted. Implement a solution that enforces mutual TLS authentication between pods.
a. You need to ensure that all communication between pods within the cluster is encrypted. Implement a solution that enforces mutual TLS authentication between pods.
CKS Exam Question 4
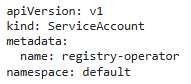
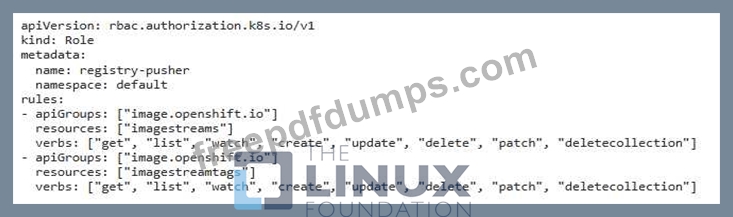
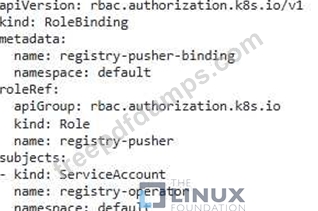
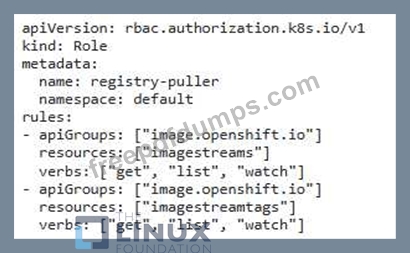
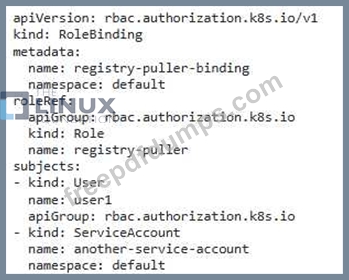
You are a security engineer tasked with securing your organization's container registry. You need to ensure that only authorized users can push images to the registry, while other users can only pull them. Explain how you would implement this using RBAC in Kubernetes and provide a detailed configuration example.
CKS Exam Question 5
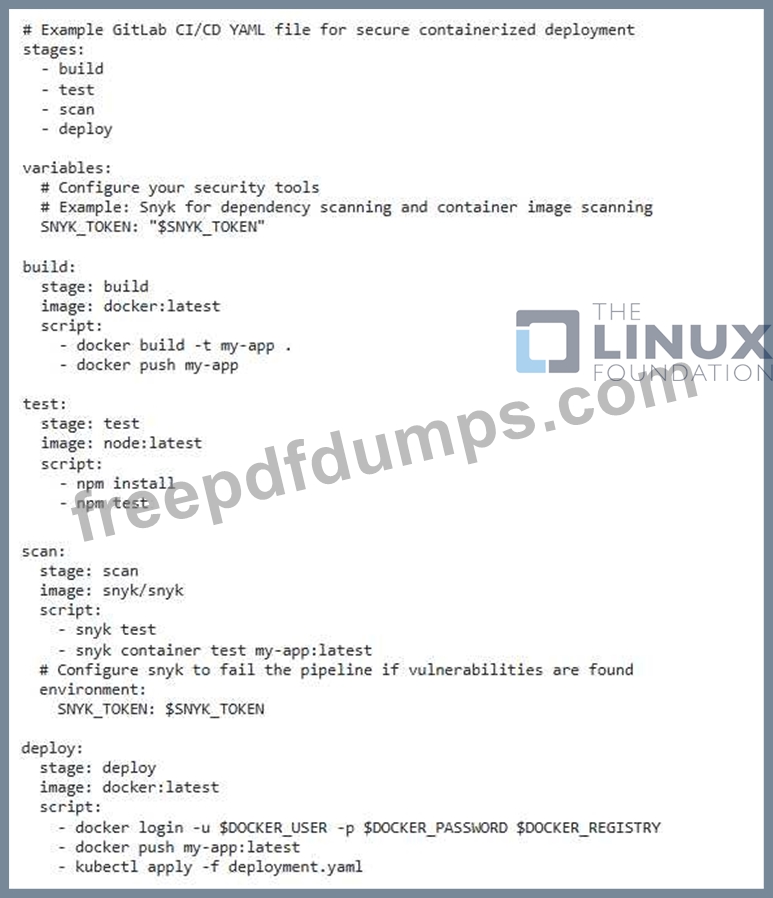
You need to implement a secure CI/CD pipeline for building and deploying containerized applications to a Kubemetes cluster. The pipeline should include security checks and validation steps at each stage to minimize the risk of introducing vulnerabilities. What security best practices would you follow?