CKS Exam Question 21
You are running a Kubernetes cluster with a number of applications deployed. You want to monitor your applications for suspicious activities and potential security breaches.
How would you implement a monitoring and logging solution that enables you to detect and respond to security threats?
How would you implement a monitoring and logging solution that enables you to detect and respond to security threats?
CKS Exam Question 22
Your Kubernetes cluster iS running a web application that requires access to a database hosted on an external Cloud provider. Describe how you can secure the connection between the application and the database using TLS/SSL encryption and identity-based authentication.
CKS Exam Question 23
You are responsible for hardening a Kubernetes cluster hosting sensitive financial data. One of the key security concerns is preventing data exfiltration. How can you use Kubernetes Network Policy to enforce network isolation and prevent unauthorized data access?
CKS Exam Question 24
You are managing a Kubernetes cluster where workloads are spread across multiple nodes- You want to configure Pod Security Policies PSPS to restrict the use of privileged containers and limit the ca abilities of containers running within your cluster.
CKS Exam Question 25
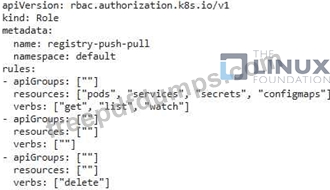
You are managing a Kubernetes cluster that uses a private Docker registry for storing container images. You need to secure the registry by restricting access to authorized users and teams. Design a solution using role-based access control (RBAC) to enforce the following policies:
- Developers in the "dev" team should be allowed to push and pull images to the registry.
- Operations team members should only be allowed to pull images.
- Security team members should have read-only access to the registry's metadata
- Developers in the "dev" team should be allowed to push and pull images to the registry.
- Operations team members should only be allowed to pull images.
- Security team members should have read-only access to the registry's metadata