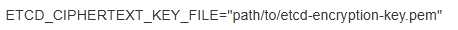CKS Exam Question 11
You have a Kubernetes cluster with a deployment named 'myapp' that serves a web application. You want to secure the application by implementing HTTPS using Ingress and TLS certificates. You have Obtained a TLS certificate from Let's Encrypt and stored it in a Kubernetes secret named 'Ietsencrypt-cert'. Configure an Ingress resource to expose the application on the domain 'myapp.example.com' with HTTPS enabled, using the 'letsencrypt-celt' secret.
CKS Exam Question 12
You are tasked with hardening the security of your Kubernetes cluster by following the CIS Kubernetes Benchmark. You need to implement a solution for securing the etcd cluster using a strong encryption at rest configuration. Explain the steps involved, including the configuration changes required in the etcd cluster and any relevant configuration changes in the Kubernetes control plane.
CKS Exam Question 13
You are deploying a critical application that handles sensitive user dat
a. Your security policy mandates that only specific system calls are allowed for the application container You decide to use seccomp to enforce this policy- Design a seccomp profile that allows only the following system calls: 'read', 'write', 'open', 'close', 'stat', 'fstat' , 'Istat' , 'getpid', 'getuid', 'getgidS , and 'exit_group'.
a. Your security policy mandates that only specific system calls are allowed for the application container You decide to use seccomp to enforce this policy- Design a seccomp profile that allows only the following system calls: 'read', 'write', 'open', 'close', 'stat', 'fstat' , 'Istat' , 'getpid', 'getuid', 'getgidS , and 'exit_group'.
CKS Exam Question 14
You are setting up a Kubernetes cluster that requires strong security measures. You need to implement several security best practices, including.
- Pod Security Policy: Implement a default Pod Security Policy that restricts resource requests, limits privilege escalation, and disables container root access.
- Network Policy: Configure network policies to restrict communication between pods within the cluster, enforcing a principle of least privilege.
- Admission Controller: Use the 'PodSecurityPolicys admission controller to enforce the defined Pod Security Policy rules.
How would you set up a secure Kubernetes cluster, including the configuration of a default Pod Security Policy, network policies, and the 'PodSecuntyP01icy' admission controller, to enforce these security best practices?
- Pod Security Policy: Implement a default Pod Security Policy that restricts resource requests, limits privilege escalation, and disables container root access.
- Network Policy: Configure network policies to restrict communication between pods within the cluster, enforcing a principle of least privilege.
- Admission Controller: Use the 'PodSecurityPolicys admission controller to enforce the defined Pod Security Policy rules.
How would you set up a secure Kubernetes cluster, including the configuration of a default Pod Security Policy, network policies, and the 'PodSecuntyP01icy' admission controller, to enforce these security best practices?
CKS Exam Question 15
Your organization has adopted a microservices architecture. Each microservice is deployed as a Kubernetes pod, and the communication between them relies neavily on service discovery and network policies. You need to implement a security measure to prevent unauthorized pods from accessing sensitive data stored within other pods. What techniques would you use and how would you apply them in a Kubernetes environment?