CKS Exam Question 31
Your Kubernetes cluster runs a critical application that utilizes a private Docker registry for its container images. However, you want to implement a security best practice by leveraging an image signing mechanism for the images pushed to the registry. Describe how you can enforce image signing and verify the integrity of container images before deployment.
CKS Exam Question 32
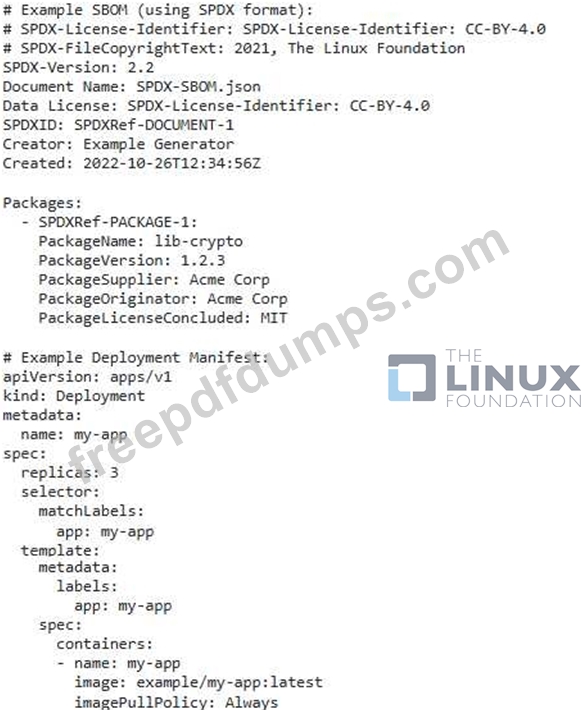
You are responsible for managing the software supply chain of a critical application deployed in a Kubernetes cluster. This application utilizes a library called 'lib-crypto' for secure cryptographic operations. How can you ensure that the version of 'lib-ctypto' deployed in your Kubernetes environment is the same as the one specified in the Software Bill of Materials (SBOM) for the application?
CKS Exam Question 33
You are building a custom Kubernetes distribution for your organization- Establish a secure process for building and verifying the integrity of the Kubernetes binaries included in your distribution.
CKS Exam Question 34
You are running a critical application in your Kubernetes cluster and want to minimize the attack surface by removing unnecessary features from the cluster- You need to identify and disable features that are not essential for your application.
CKS Exam Question 35
You are running a Kubernetes cluster with a deployment named "my-app" that has been experiencing unexpected crashes. The crash logs indicate that the container's memory consumption is exceeding the resource limits defined in the deployment YAML. Explain how you can utilize the Kubernetes resource quotas and admission controller to prevent this from happening again.