CKS Exam Question 6
You are managing a Kubernetes cluster with several deployments running different microservices. You need to ensure that all pods are running with appropriate security context constraints (SCCs) to minimize the risk of privilege escalation and other security vulnerabilities. Explain how you would implement and enforce pod security standards using SCCs, providing specific examples ot common security constraints and how you would configure them for various deployment scenarios.
CKS Exam Question 7
You have a Kubernetes cluster that runs a critical application This application uses sensitive data stored in a persistent volume that is accessible only by the pods running the application. You want to ensure that if any pod is compromised, the attacker cannot gain access to this sensitive data What security best practices would you implement?
CKS Exam Question 8
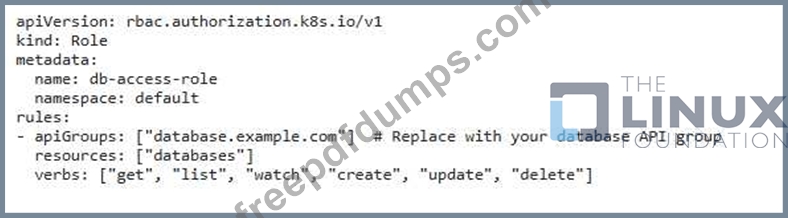
You are deploying a new application in a Kubernetes cluster that needs to access a confidential database- You want to ensure that the application container can only access the database using a dedicated service account with limited permissions. Describe how you would create and use a service account with restricted permissions for this application, ensuring the database access is secure.
CKS Exam Question 9
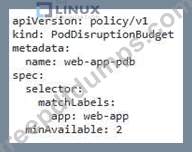
You are working on a Kubernetes cluster that has a deployment named 'web-app'. The deployment is currently running on a single node. You need to implement a pod disruption budget (PDB) for this deployment to ensure that at least 2 out of 3 pods are always available during a rolling update. How would you implement a pod disruption budget (PD8) to achieve this, and what commands would you use to ensure that at least 2 out of 3 pods are always available during a rolling update.
CKS Exam Question 10
You have a multi-tenant Kubernetes cluster where each tenant has its own namespace. You need to configure security policies to ensure that:
- Pods in namespace 'tenant-a' cannot access any resources in namespace 'tenant-b'
- Pods in namespace 'tenant-b' can access resources in namespace 'tenant-a' only if they have a label 'tier:gold'.
- Pods in namespace 'tenant-a' cannot access any resources in namespace 'tenant-b'
- Pods in namespace 'tenant-b' can access resources in namespace 'tenant-a' only if they have a label 'tier:gold'.