CKS Exam Question 26
Describe now you would design a security posture for a Kubernetes cluster using the CIS Kubernetes Benchmark as a guideline. Include key areas to focus on, relevant security controls, and how you would monitor and enforce compliance with the benchmark.
CKS Exam Question 27
Your organization uses Kubernetes to run a microservice application. One of the microservices is a payment gateway that processes sensitive payment information. How would you implement security measures to protect this payment gateway microservice and minimize the risk of data breaches, considering the security requirements are very stringent?
CKS Exam Question 28
You are tasked with securing the container image supply chain for your organization_ You are using a container registry that supports signing and verification of container images. You need to create a policy that ensures only signed images from a specific trusted source are deployed to your Kubernetes cluster.
CKS Exam Question 29
You have a Kubernetes cluster with a Deployment named 'secure-app-deployment running a sensitive application. You want to ensure that only authorized users can access the application's pods and its sensitive data.
How would you use Role-Based Access Control (RBAC) to restrict access to the 'secure-app-deployment' and its resources?
How would you use Role-Based Access Control (RBAC) to restrict access to the 'secure-app-deployment' and its resources?
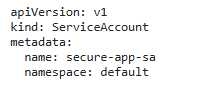
CKS Exam Question 30
You're tasked With securing a Kubernetes cluster for a sensitive application. The application utilizes a service account for accessing a database. However, due to legacy reasons, this service account has broad permissions, including 'read', 'write', and 'delete' access to all resources in the cluster. How would you mitigate this security risk while maintaining application functionality? Implement a solution that minimizes the permissions granted to the service account and adheres to the principle of least privilege.