CKS Exam Question 56
You are deploying a Kubernetes cluster on AWS using EKS. verify the authenticity and integrity of the AWS CLI and EKS platform binaries before interacting with your cluster:
CKS Exam Question 57
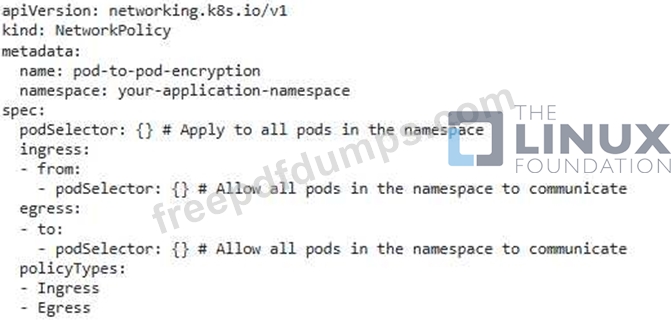
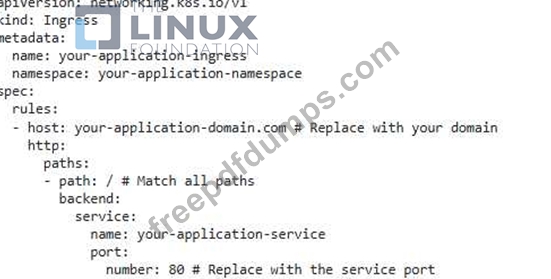
You have a Kubernetes cluster running on a public cloud provider. You're deploying a microservice application that handles sensitive user data To enhance security, you need to implement Pod-to-Pod encryption using Cilium. This encryption should be applied to all communication between pods within your application's namespace. How would you configure Cilium to achieve this, while also ensuring that you can still access the application from outside the cluster through a dedicated Ingress service?
CKS Exam Question 58
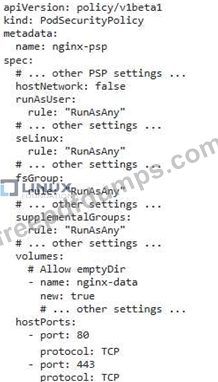
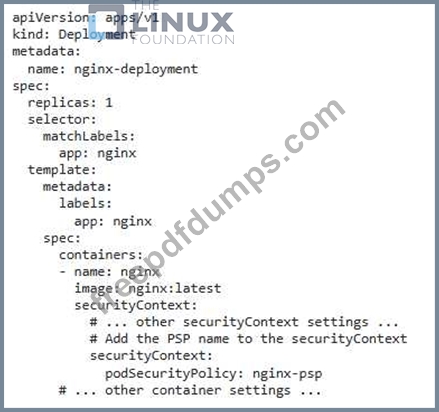
You have an Nginx pod deployed in your Kubernetes cluster. You need to set up a PodSecurityPolicy (PSP) that allows the Nginx pod to access only specific network ports and disallows it from accessing other ports. Describe the steps you would take to implement this PSP.
CKS Exam Question 59
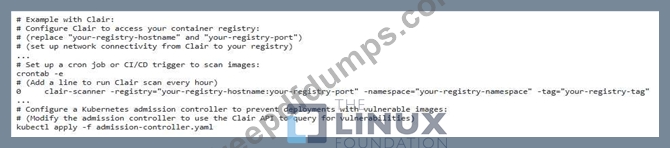
Your Kubernetes cluster utilizes a container registry hosted on-premise. You want to implement a mechanism to automatically scan images stored in this registry for known vulnerabilities before they are deployed to the cluster. Describe the steps involved in setting up this vulnerability scanning process.
CKS Exam Question 60
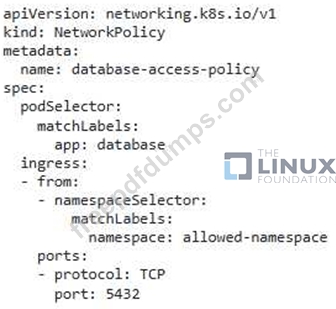
Your Kubernetes cluster runs a Deployment named 'database' which exposes a database service. You need to implement a NetworkPolicy that allows only pods belonging to a specific namespace to access the database service.