CKS Exam Question 51
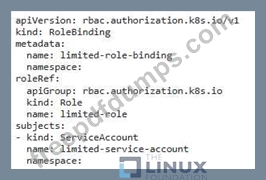
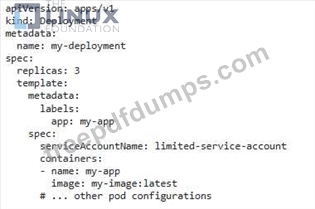
You are tasked with securing a Kubernetes cluster that runs sensitive workloads. You need to implement a mechanism to enforce least privilege access for all pods in the cluster.
CKS Exam Question 52
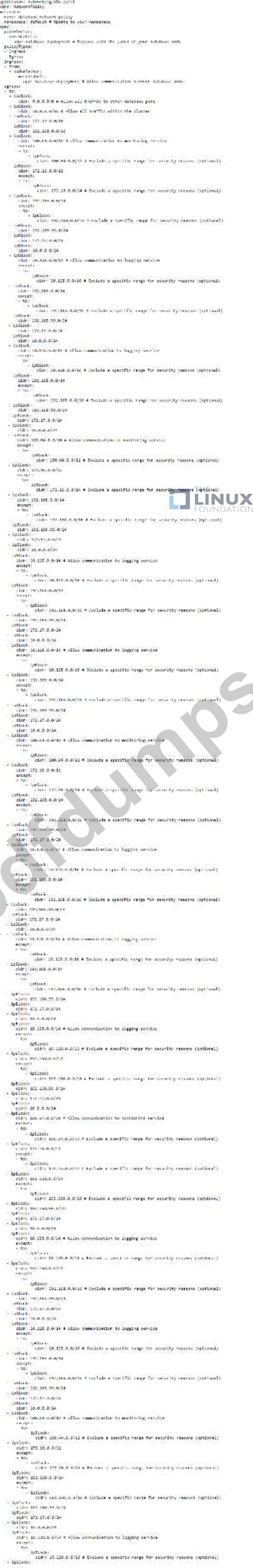
You are managing a Kubernetes cluster with a deployment named 'database-deployment' running 3 replicas of a PostgreSQL database container. You need to implement a security policy that restricts the database pods from accessing the internet, allowing them to only communicate with each other and with specific external services. The allowed external services include a dedicated monitoring service at 'monitoring-example-com:8080' and a logging service at 'logging-example-com:514'. Additionally, you want to enforce this policy using NetworkPolicy.
CKS Exam Question 53
You are running a microservices application on Kubernetes where each service is deployed as a separate Deployment. You want to implement multi-tenancy to ensure that different tenants nave their own isolated environments. How would you implement this multi-tenancy strategy, and what are some of the potential challenges?
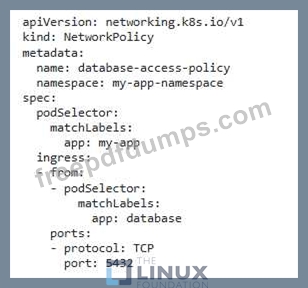
CKS Exam Question 54
You have a Pod that runs an application that accesses a database service running in a different namespace. You want to enforce a rule that only allows the pod to connect to the database service on a specific port. Explain how to achieve this using NetworkPolicy.
CKS Exam Question 55
You are using a third-party Helm chart to deploy an application to your Kubernetes cluster. You need to ensure that the Helm chart adheres to security best practices and does not introduce any vulnerabilities into your cluster. Implement a solution that uses KubeLinter to statically analyze the Helm chart before deployment.