CKS Exam Question 61
You are running a web application in a Kubernetes cluster using a Deployment named 'web-apps. The application is vulnerable to a known CVE that can be exploited through tne web server. You need to implement a security policy to prevent pods from accessing the vulnerable web server port.
CKS Exam Question 62
You are building a container image for a critical application that needs to be deployed in a Kubernetes cluster. Your organization has strict security policies in place, requiring you to perform a thorough security audit of the image before deployment. Outline the steps you would take to conduct a comprehensive security audit of the container image, focusing on the following aspects:
- Vulnerability Scanning: Use tools to scan the image for known vulnerabilities and provide details of the process.
- Security Best Practices: Describe the security best practices that you would audit against.
- Runtime Behavior Analysis: Explain how you would analyze the image's runtime behavior to identify potential risks.
- Vulnerability Scanning: Use tools to scan the image for known vulnerabilities and provide details of the process.
- Security Best Practices: Describe the security best practices that you would audit against.
- Runtime Behavior Analysis: Explain how you would analyze the image's runtime behavior to identify potential risks.
CKS Exam Question 63
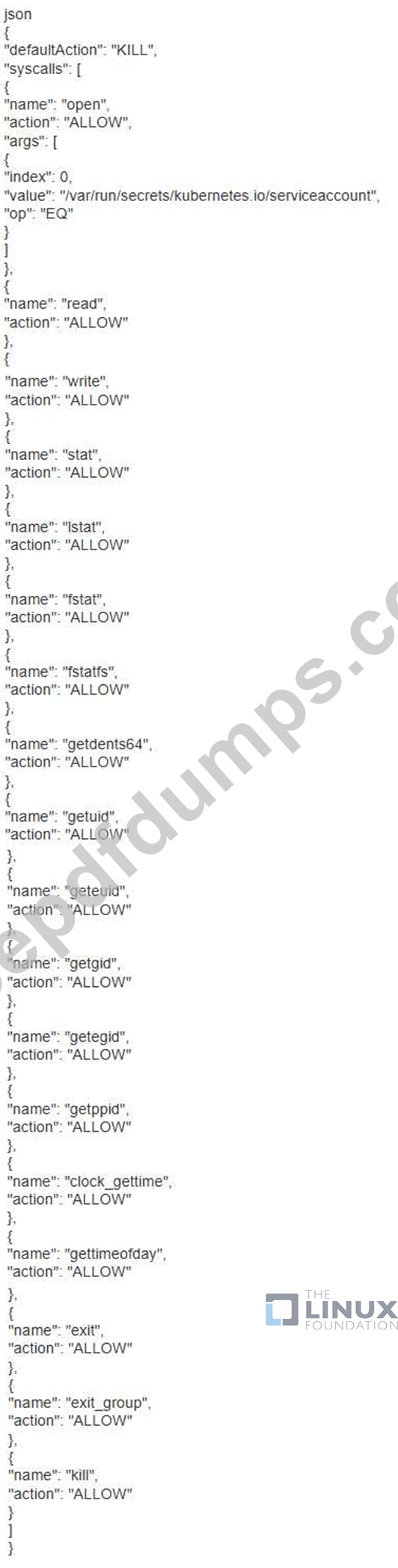
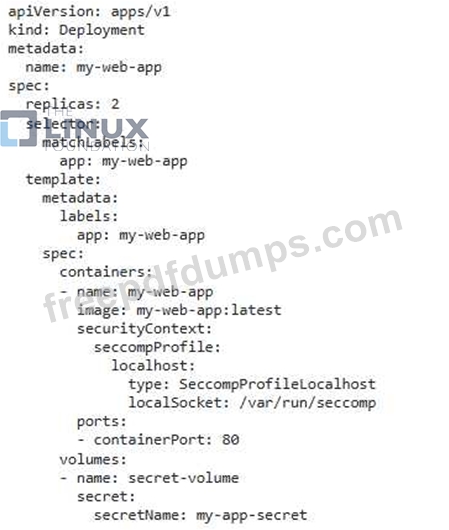
You are running a web application in a Kubernetes cluster using a Deployment. You want to implement a security measure to ensure that the application container only has access to the necessary system calls and files. You're worried about potential exploits that could give the container excessive privileges. Explain how you would use Seccomp profiles to achieve this, and provide an example Seccomp profile using a JSON format.
CKS Exam Question 64
You are using a container image signed by a trusted entity. Describe the steps involved in verifying the signature of the image during the image pull process in Kubernetes.
CKS Exam Question 65
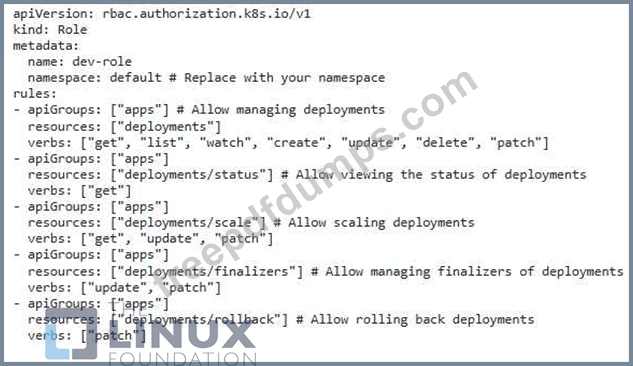
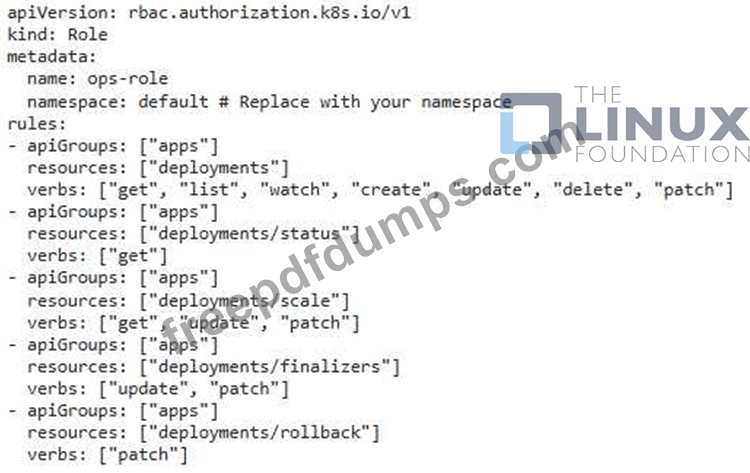
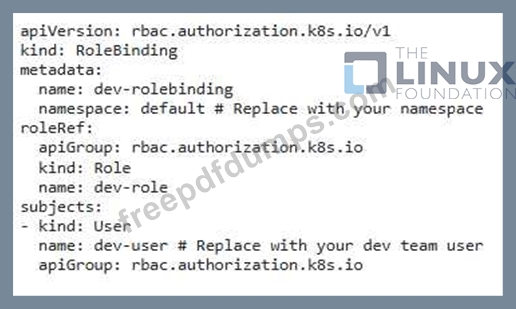
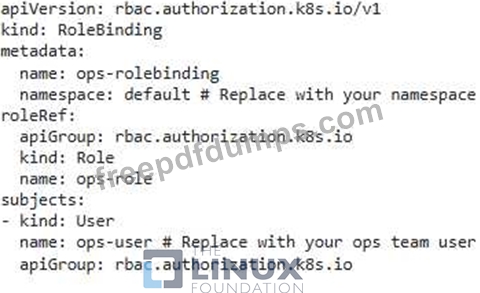
You have a Kubernetes cluster running an application with multiple deployments. You want to implement RBAC rules to ensure that only specific users can manage the deployments belonging to their respective teams. For instance, the "dev" team should only be able to manage deployments With the label 'team: dev' , while the "ops" team should only manage deployments With the label steam: 'ops'.