CKS Exam Question 66
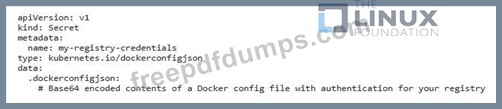
You are tasked with securing a Kubernetes cluster running a critical application. One of the security best practices you need to implement is to enforce the use of signed container images. You have access to a private container registry and a PKI system for generating and managing certificates. Explain in detail now you would implement this policy, covering steps like image signing, verification, and integration with Kubernetes.
CKS Exam Question 67
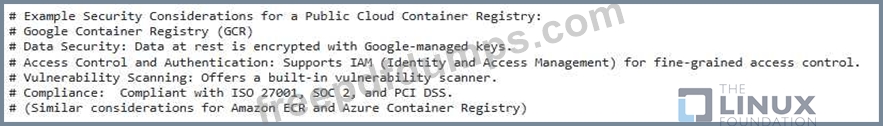
You are deploying a Kubernetes cluster in a public cloud environment and are considering using a managed container registry service offered by the Cloud provider. What are the security considerations you Should take into account before Choosing a managed container registry service?
CKS Exam Question 68
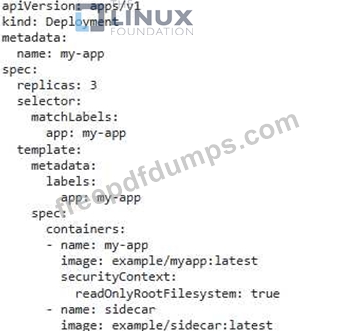
You have a microservice application running in a Kubernetes cluster with a sidecar container responsible for logging. The sidecar container has access to the main application containers sensitive data, including credentials. You need to implement a security policy to prevent the sidecar container from accessing the main application container's data.
CKS Exam Question 69
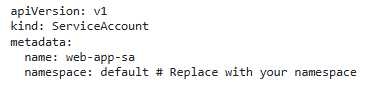
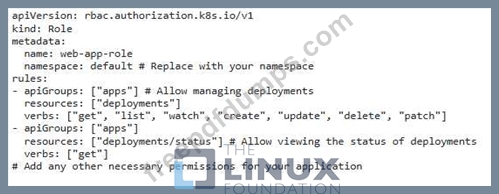
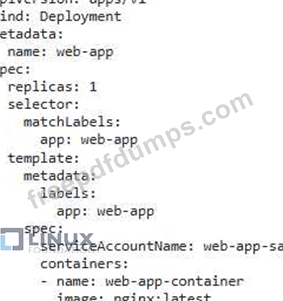
You have a Kubernetes cluster running a web application deployment named 'web-app' that uses a service account called 'web-app-sa' The 'web-app-sa' has been granted the necessary RBAC roles and permissions to access specific resources in the cluster. You want to implement a strategy to prevent the 'web-app' deployment from using unauthorized service accounts that might be accidentally created or added to the deployment spec.
CKS Exam Question 70
You are running a Kubernetes cluster with a deployment named "my-app" that uses a container image from a public registry. You suspect that a recent deployment update may have introduced a vulnerability in one of the containers. Describe how you can use container image scanning tools like Trivy to identify and address the vulnerability.