CKS Exam Question 46
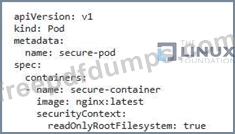
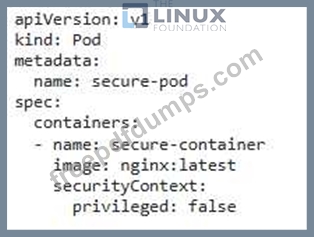
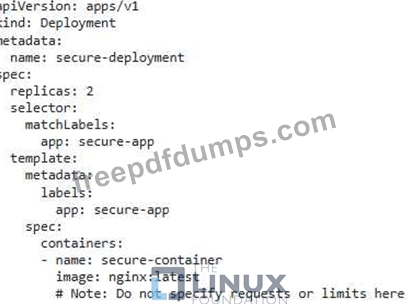
You are tasked with securing a Kubernetes cluster that runs sensitive workloads. To prevent unauthorized access, you need to ensure container immutability at runtime. How would you implement a solution that prevents any modifications to the running containers once they are launched? Provide a detailed breakdown of the steps and configurations you would use.
CKS Exam Question 47
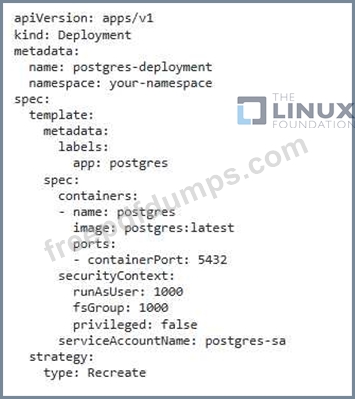
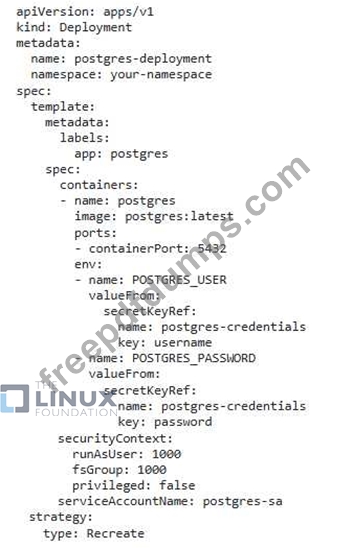
You are running a critical application within a Kubernetes cluster, and you need to implement a robust security posture to prevent unauthorized access and protect sensitive dat
a. The application uses a PostgreSQL database, and you want to enforce strong access control for the database while ensuring the database pods are not directly accessible from the internet Describe how you would implement the following security measures using Kubernetes resources and tools:
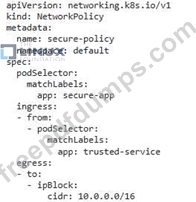
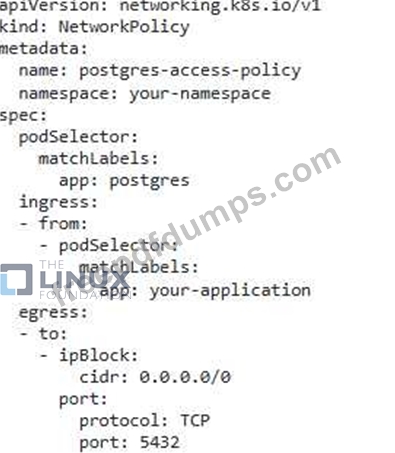
1. Network Policy: Create a network policy that restricts access to the PostgreSQL database pods to only the application pods.
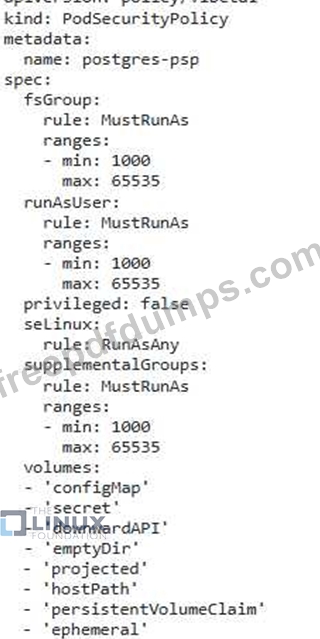
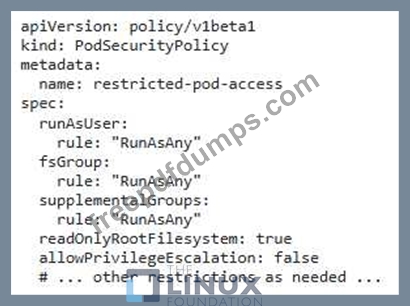
2. Pod Security Policies: Enforce strong security policies for the database pods, including restrictions on capabilities, resource usage, and privileged
access.
3. Secret Management Securely store the database credentials using a Kubernetes secret, ensuring that only authorized application pods can access
them.
4. Logging and Monitoring: Implement logging and monitoring for the PostgreSQL database pods to detect any potential security threats or anomalies.
a. The application uses a PostgreSQL database, and you want to enforce strong access control for the database while ensuring the database pods are not directly accessible from the internet Describe how you would implement the following security measures using Kubernetes resources and tools:
1. Network Policy: Create a network policy that restricts access to the PostgreSQL database pods to only the application pods.
2. Pod Security Policies: Enforce strong security policies for the database pods, including restrictions on capabilities, resource usage, and privileged
access.
3. Secret Management Securely store the database credentials using a Kubernetes secret, ensuring that only authorized application pods can access
them.
4. Logging and Monitoring: Implement logging and monitoring for the PostgreSQL database pods to detect any potential security threats or anomalies.
CKS Exam Question 48
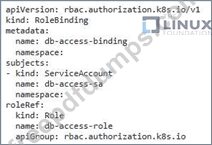
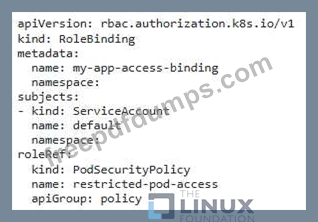
You have an application running in a Kubernetes cluster that requires access to a database hosted in a different namespace. You want to implement a secure mecnanism to allow the application to access the database witnout granting it access to all resources in the database namespace.
CKS Exam Question 49
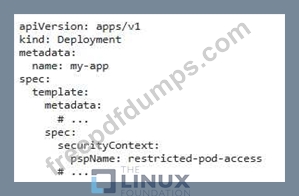
You are managing a Kubernetes cluster With various security measures in place. You have a deployment named 'my-apps that uses the default service account for its pods. To ensure that only authorized users can access the pods running in the 'my-app' deployment, implement a security policy that restricts access to tne pods based on user identity.
CKS Exam Question 50
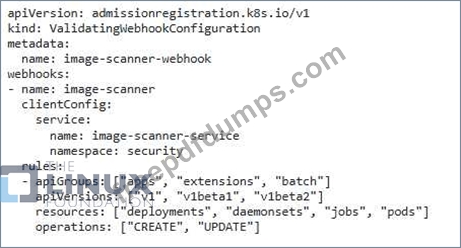
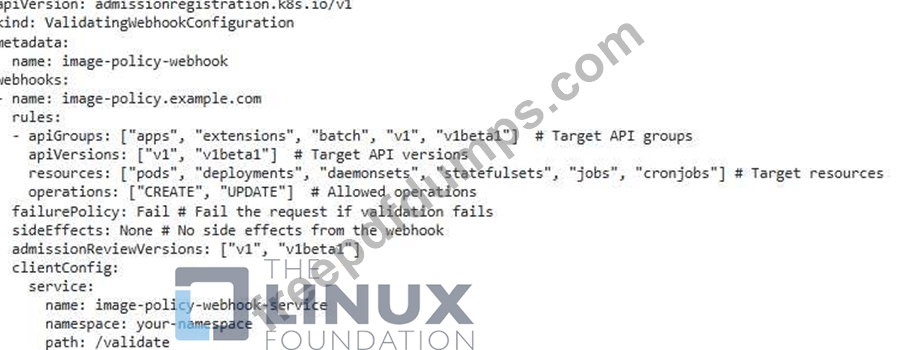
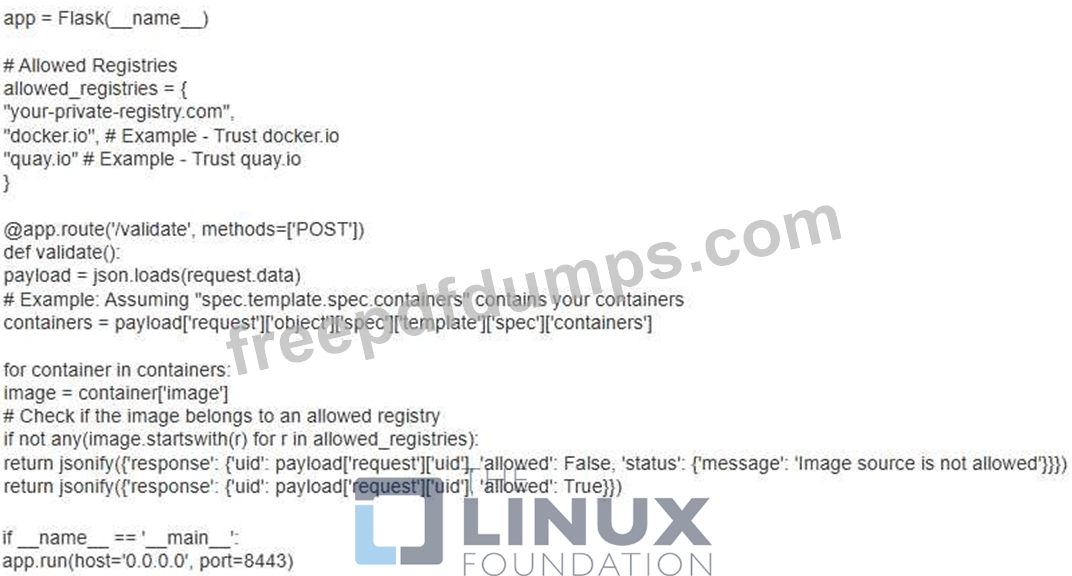
You're designing a security policy for your Kubernetes cluster to restrict container image sources. You want to allow only images from your private registry and a few trusted public registries. How would you implement this policy using Admission Webhooks and what kind of validation logic would you implement in the webhook?