CKS Exam Question 71
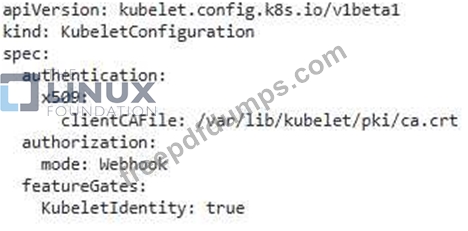
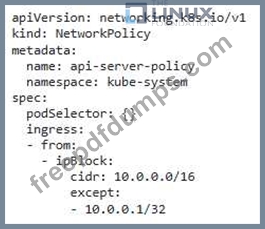
You are tasked with securing a Kubernetes cluster that runs a critical web application. The cluster iS deployed on AWS and uses a custom API server for authentication You are required to implement a security strategy that enforces strong authentication and authorization for accessing the Kubernetes API, while also minimizing the attack surface.
CKS Exam Question 72
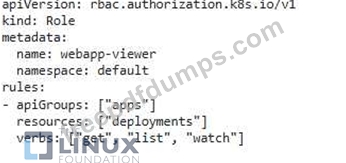
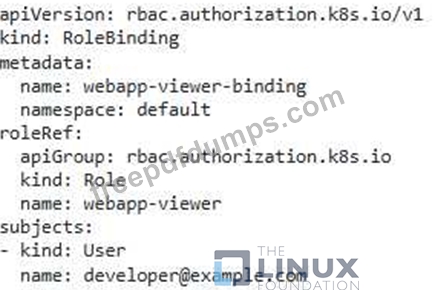
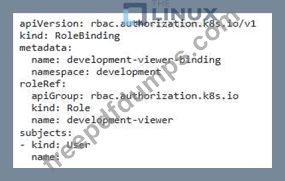
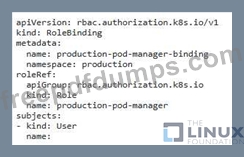
You have a Kubernetes cluster running with the default RBAC configuration. You need to create a role that allows a user to access only specific namespaces and perform certain actions within those namespaces. For example, you want to allow the user to view pods, deployments, and services in the 'development namespace, but only allow them to create and delete pods in the 'productions namespace.
CKS Exam Question 73
You are working on a Kubernetes cluster that hosts a critical microservices application. You have identified that the application is vulnerable to a known attack vector through a specific service called "payment-service." You need to quickly implement a security measure to mitigate this attack vector while minimizing the impact on other services.
How can you use a network policy to isolate the "payment-service" from the rest of the cluster and prevent the attack without disrupting the normal functioning of other microservices?
How can you use a network policy to isolate the "payment-service" from the rest of the cluster and prevent the attack without disrupting the normal functioning of other microservices?
CKS Exam Question 74
You are running a Kubernetes cluster with a deployment named "my-app" that uses a container image from a public registry. You suspect that a recent deployment update may have introduced a vulnerability in one of the containers. You want to apply a security patch to the container image Without rebuilding it. Explain now you would implement this using a container patching tool like 'kpatch' and update the deployment.
CKS Exam Question 75
You are tasked with hardening a Kubernetes cluster running on a public cloud provider. The cluster currently runs Kubernetes version 1.18 and has been exposed to the internet for several months. A security audit has identified several vulnerabilities in the current Kubernetes version, including CVE-2021-25743, which affects all versions prior to 1.22.
How do you upgrade your cluster to Kubernetes 1.22 and patch the vulnerabilities without disrupting the applications running on the cluster?
How do you upgrade your cluster to Kubernetes 1.22 and patch the vulnerabilities without disrupting the applications running on the cluster?